# Background:
Since at least 2018, North Korea has deployed thousands of it's citizens overseas in order to secure work in high paying IT jobs as a way of generating vast revenue streams for it's nuclear weapons program. The DPRK's IT Workers do this by using fake identities to obtain employment as developers around the world and utilize an expansive criminal network involving identity fraud, shell companies, "laptop mules", generative AI, and a vast amount of illicit underground services. In a United Nations Council of Experts report, one freelance platform stated that they believed the vast majority of skilled cryptocurrency developers online were in fact DPRK IT Workers. The platform additionally stated that they believed some newer freelance platforms may have actually been created by the DPRK to facilitate employment of their workers. There have been numerous press releases by the US Department of Justice in recent years detailing how American citizens have been paid to host "laptop farms" for IT workers, assist them in finding employment, and set up remote access methods to mask their locations. The threat of IT Workers only continues to grow as time goes on. They are known to identify, build, and exploit vulnerabilities in smart contracts, and are suspected of carrying out several heists over the past two years, as documented by ZachXBTand others. In July, 2024, the security company KnowBe4 documented how they inadvertently hired an IT Worker who preceded to load malware onto their company laptop directly after onboarding. Mandiant's Michael Barnhart stated on an episode of the Defender's Advantage Podcast, titled "The North Korean IT Workers", that North Korean operators such as Park Jin Hyok, who participated in the Sony hack and WannaCry, have also been seen posing as freelancers online. Contrary to some online discussion, North Korean IT Workers are real and widespread. They use sophisticated and illicit means to bypass enterprise-level background checks which most companies and online projects have no means of implementing, and face almost no real consequences when caught. There is an estimated 10,000 IT Workers stationed around the world, with each of them building and utilizing multiple fake identities and personas. It is thus not difficult to imagine the scale and amount of noise that these operations cause downstream. The IT Workers are an incredibly unique threat and operate very differently than most threat actors who make the headlines. They blend the methods of real world organized crime with the cybercriminal, all the while having nation state backing and capability. While most IT Workers will focus on carrying out their job functions, the levels of access that they are given after being hired is what many cybercrime and APT groups will spend months to obtain, and poses considerable risk. To better document how North Korean IT Workers operate, we've analyzed and documented findings from infostealer logs originating from 5 of their computers.
# Introduction:
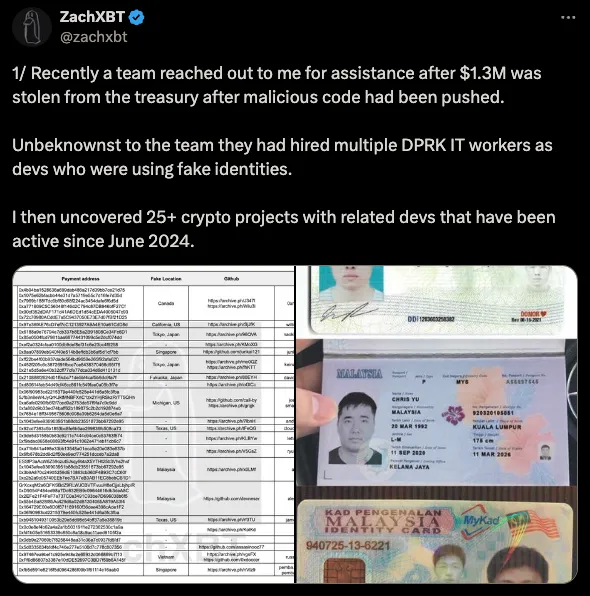
These findings are primarily thanks to ZachXBT's investigation and @superducktoes, who gave us invaluable insight into NetKey (covered later) and throughout the entire writing process. After pivoting off of indicators from ZachXBT's investigation, we were able to identify roughly 1,300 emails and 5 sets of stealer logs, which we have high confidence belong to DPRK IT Workers. While we plan to delve deeper into the emails at a later point, the scope of this post is solely on the stealer logs. The stealer logs discovered were from Raccoon Stealer and potential RedLine infections. Four out of the five originate from Khabarovsk, Russia, and were infected in 2020. The last IT worker's IP geolocates to Hong Kong and was infected in 2021. Note that these locations come with some caveats that will be discussed in the next section, but we will continue to refer to these as their locations for sake of clarity. Although there were sadly no particularly interesting files stolen from these hosts, the logs do still give some interesting insights that allow us to better understand the scale and behaviors of DPRK IT Workers.
# The Mysterious Case of NetKey

Before we continue, it's important to note that the first noticeable commonality between all of the stealer logs is an installed application called NetKey. Though "NetKey" sounds fairly generic, we found very little information about it online, and yet, it is where the aforementioned caveat originates from. All of the hosts from Khabarovsk had NetKey v4.0/4.1 installed, while the Hong Kong host had NetKey v5.0 installed. The only relevant mentions of NetKey we could find are from the NKInternet Blog and a Twitter thread from 2019 where a piece of malware, believed to be targeting the DPRK, makes a reference to a potential NetKey DLL. After talking more about NetKey with @superducktoes, we learned that NetKey is believed to be used as the authentication utility for accessing the external internet from within North Korea. This is interesting. Why? IT Workers are believed to be primarily stationed outside of North Korea, and yet most of the infected hosts had external IPs not publicly associated with the DPRK. Some recent leak files from a North Korean server, posted on Twitter by @BizzareDect and documented by 38North, provided some additional insight into NetKey in the form of a receipt from 2019 between an unknown overseas joint venture and Pyongyang Internet Communications.
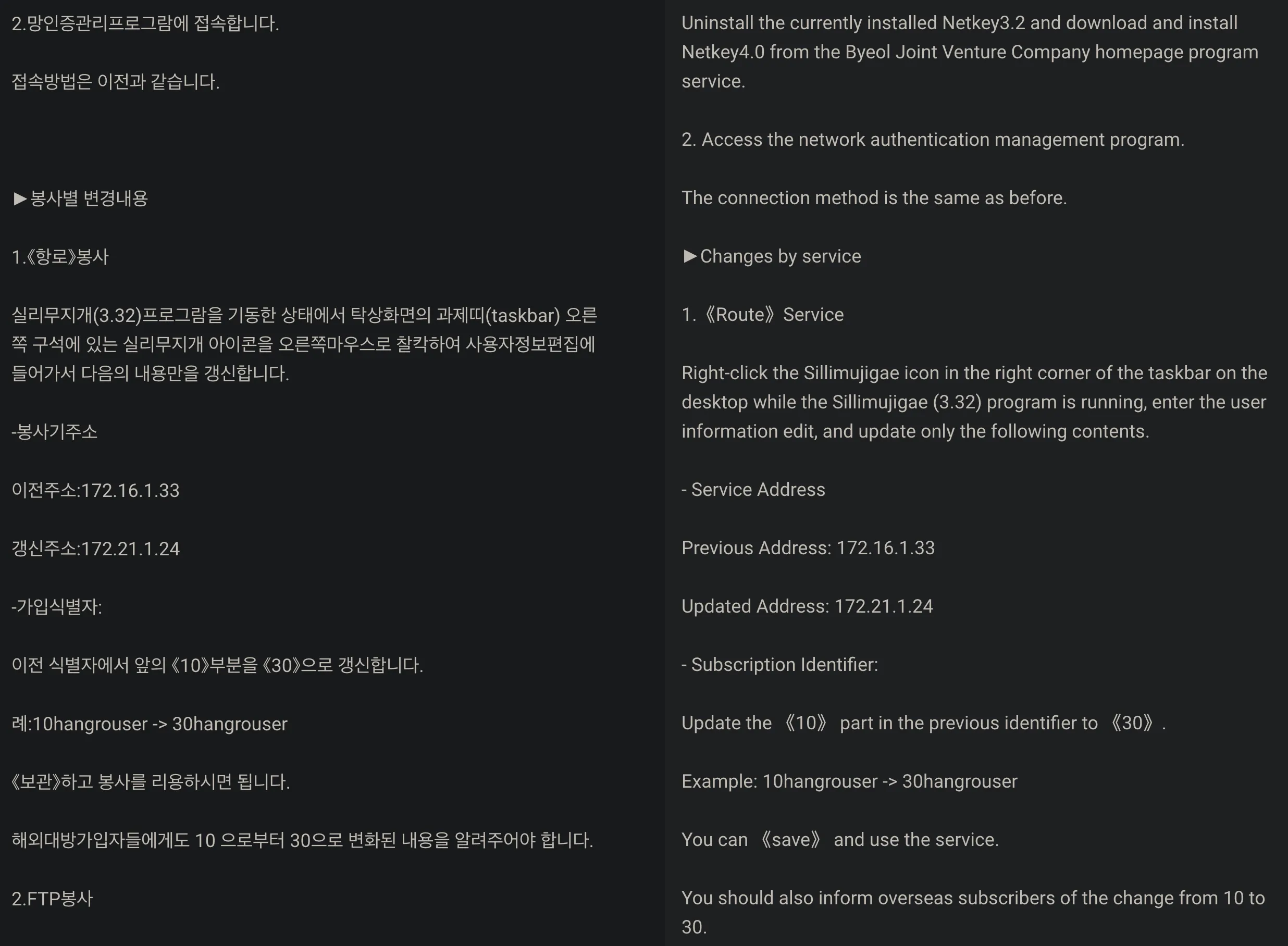
The above screenshot details steps that must be taken to use some sort of "new system". While it's not entirely clear which system is being referenced, the receipt's instructions involve installing a new version of NetKey, which the receipt notes, also applies to "overseas subscribers". This finding was fairly recent, but makes us think that NetKey has, and is being, used from abroad to access Kwangmyong, North Korea's intranet. The IPs seen were also interesting. The infected hosts showing external IPs in Khabarovsk all originated from a /24 range within TransTeleCom (AS20485)'s IP space. TransTeleCom started providing an internet connection to North Korea in 2017, and although the /24 range in the stealer logs is not publicly associated with the DPRK, the NKInternet blog also noted that it at some point had shared certificates used in known North Korean IP ranges. The Hong Kong host showed a more direct connection to DPRK IP space as it's ASN directly peers with Ryugyong-dong (AS131279), North Korea's primary AS. Due to the points listed above, and the fact that NetKey appeared to be active at time of infection, we're of the opinion that the geolocations tied to these infections are not indicative of the actual location these IT Workers operate from. However, we'll still continue to refer to these stealer logs by their IP geolocation.
# The Logs:
## System Info:
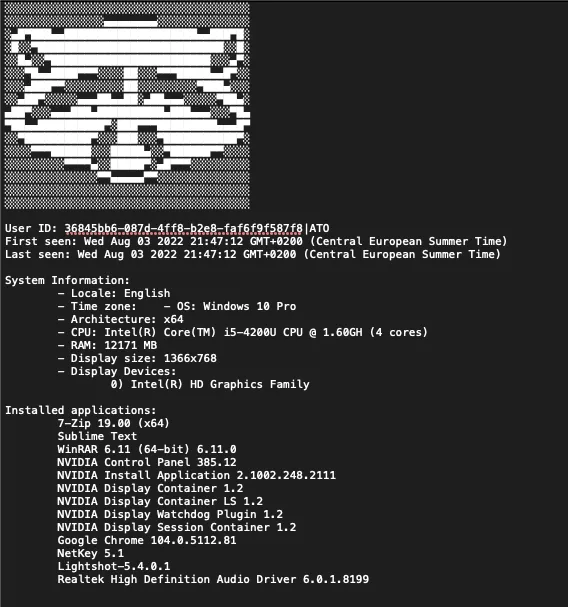
Across the 5 sets of stealer logs there was 187 total login items found, with the most common being for mail providers, Github, and freelancer sites such as UpWork, Habr, and Guru, as well as web and cryptocurrency education platforms. There were also login and cookie items present for SANS, gaming websites, cybersecurity platforms, hosting providers, and gambling sites. Installed keyboards were largely the same across all hosts (English and Korean), with one exception for an IT Worker identified as Helios. Helios had English, Korean, Japanese, and Chinese keyboards installed and their logs, as well as OSINT, seemed to confirm that they had been working across all languages. Though no Russian keyboards were installed, some of the logs indicated operating in Russia to some capacity, with one having a login item for a Russian websites used to find and schedule doctor's appointments. The fact that IT workers operate across the world is well known, and these logs only served to reinforce that. While most public reporting seems to focus on their employment in the United States and South Korea, many operate in Japan and have been observed in Russia and across the European Union. Since their goal is mass revenue generation, they will likely take any position they can get -- no matter the location. It does, however, seem that some personas are made to target specific countries and locations. Beyond NetKey, the list of installed applications provided some insights into how IT Workers operate and their different focuses. One application installed across 3 of the Khabarovsk hosts, called "IP Messenger for Win", allows messaging between users on the same LAN and may indicate some form of collaboration between workers in the same units. Additionally, the presence of IP Messenger on these hosts is an indicator in itself, as the application is purportedly very popular within the DPRK. RDP, PDF editing, Virtual Machine, and software development applications were common across all of the logs. One of the hosts had Azendoo installed, which is used for team management and task tracking. This may indicate that this host belonged to a higher level IT Worker in a managerial position, or that some units may use this, or similar, software to track their operations. When it comes to programming, Python and node.js were installed across 4/5 hosts, with Helios' host also having Go, F#, and additional C++ tools (such as the x64 ARM cross compiler) installed. Most of the logs showed web development applications such as XAMPP and NodeJS.
## Browser Data:
Though it has been noted that IT workers operate in heavily restricted environments, we did not observe any notable restrictions in regards to internet access.
2/5 of the hosts showed having software piracy websites opened in their browser, which seems to be the most plausible infection vector. Analyzing cookie data for most frequently visited websites largely resembles that of any freelancer or developer. Some of the most frequently appearing domains were for:
- Softonic
- UpWork
- Fiverr
- TechRadar
- Medium
- Business Insider
- Github
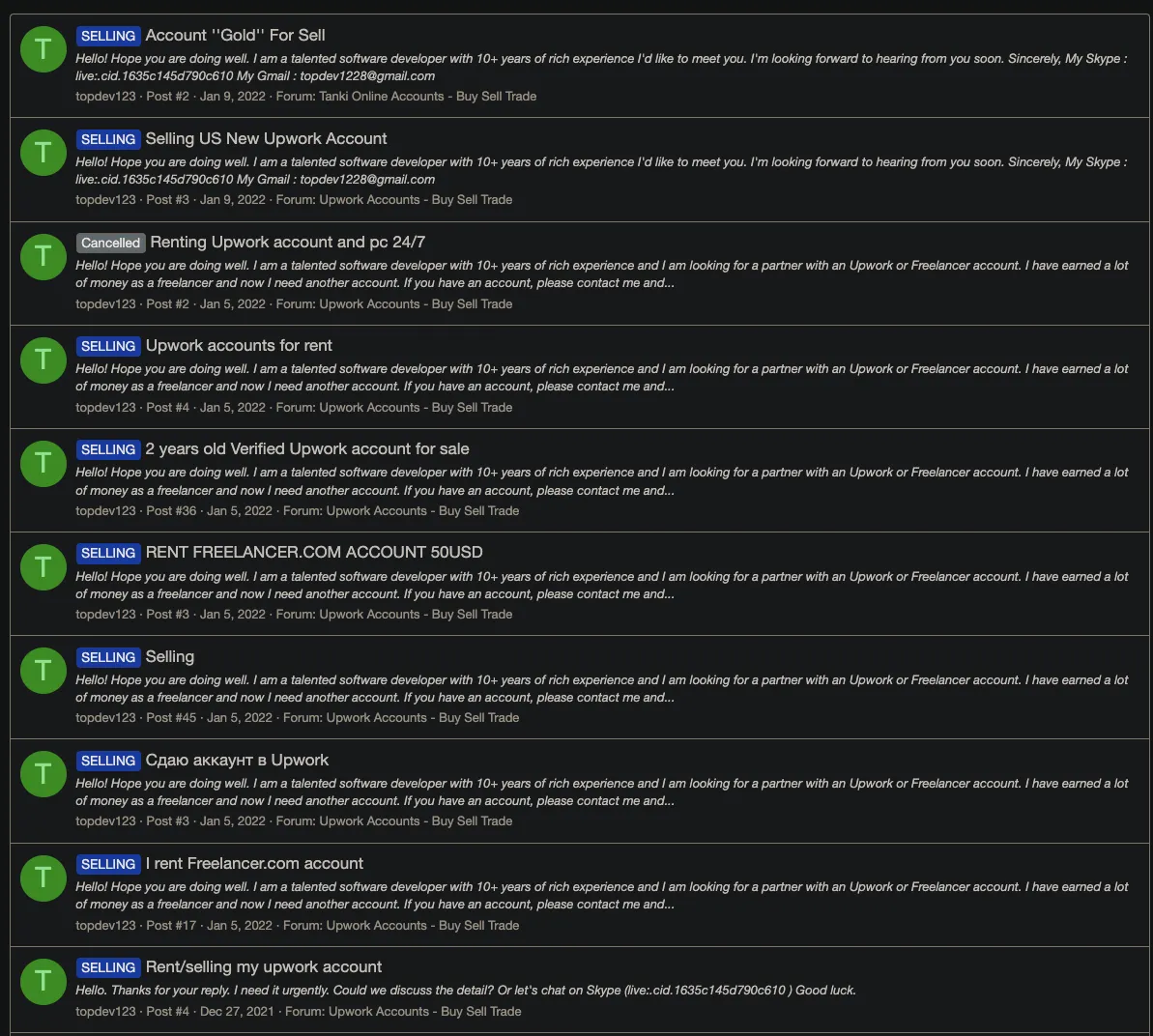 Some emails observed appeared to tie back to legitimate accounts unrelated to the IT Workers. Looking further through the data it appears that some IT Workers are active on forums such as PlayerPuff, where you can buy "aged" accounts on freelancing sites. The workers also seem aware that this activity appears suspicious -- Helios' logs contained cookie data showing that they had viewed a page on freelancer[.]com[.]ru titled: "Someone from China wants to use my Upwork account".
Some emails observed appeared to tie back to legitimate accounts unrelated to the IT Workers. Looking further through the data it appears that some IT Workers are active on forums such as PlayerPuff, where you can buy "aged" accounts on freelancing sites. The workers also seem aware that this activity appears suspicious -- Helios' logs contained cookie data showing that they had viewed a page on freelancer[.]com[.]ru titled: "Someone from China wants to use my Upwork account".
## Autofill Data:

The logs show a dizzying array of different identities, accounts, and contact information -- on average there was 16 emails per host. Many of these emails followed the same typical IT Worker patterns. Here's a small sample:
masterdev1027@gmail.com
fulldev317@gmail.com
codeknight0707@gmail.com
seniordev9726@outlook.com
dreamcomes0704@gmail.com
topdev1228@protonmail.com
helios0912@outlook.com
smartfox1203@gmail.com
"star", "dev", "pro", "senior", and "coder" are typical keywords seen in the emails, usually followed by 3 or 4 digits. Personas did not follow any real trends, although names commonly appeared to originate from English speaking countries, Japan, and Eastern Europe (mainly Ukrainian and Russian). IT Workers frequently use stolen/fake identities or the names of their overseas facilitators anyway, so they're bound to vary. LinkedIn and Github accounts were the most commonly seen outside of email, and nearly all of them had either been deleted, changed username, or otherwise disappeared. This is a fairly common trend that can be useful when investigating potential IT Workers, as most legitimate individuals won't have issues maintaining their social media accounts or at least will keep their active ones linked. IT Worker Github accounts often follow or like repositories of other IT Workers. It's often possible to work out teams or small network's just by enumerating followers, follows, and likes. There is also often commits from deleted accounts, or "About Me" repositories from worker's past accounts that they've copied over. Though there was a surprising lack of phone numbers in the autofill data, IT Workers frequently use VOIP numbers and seem to have a preference for Skype.
# Conducting OSINT on IT Worker Profiles
## Helios:
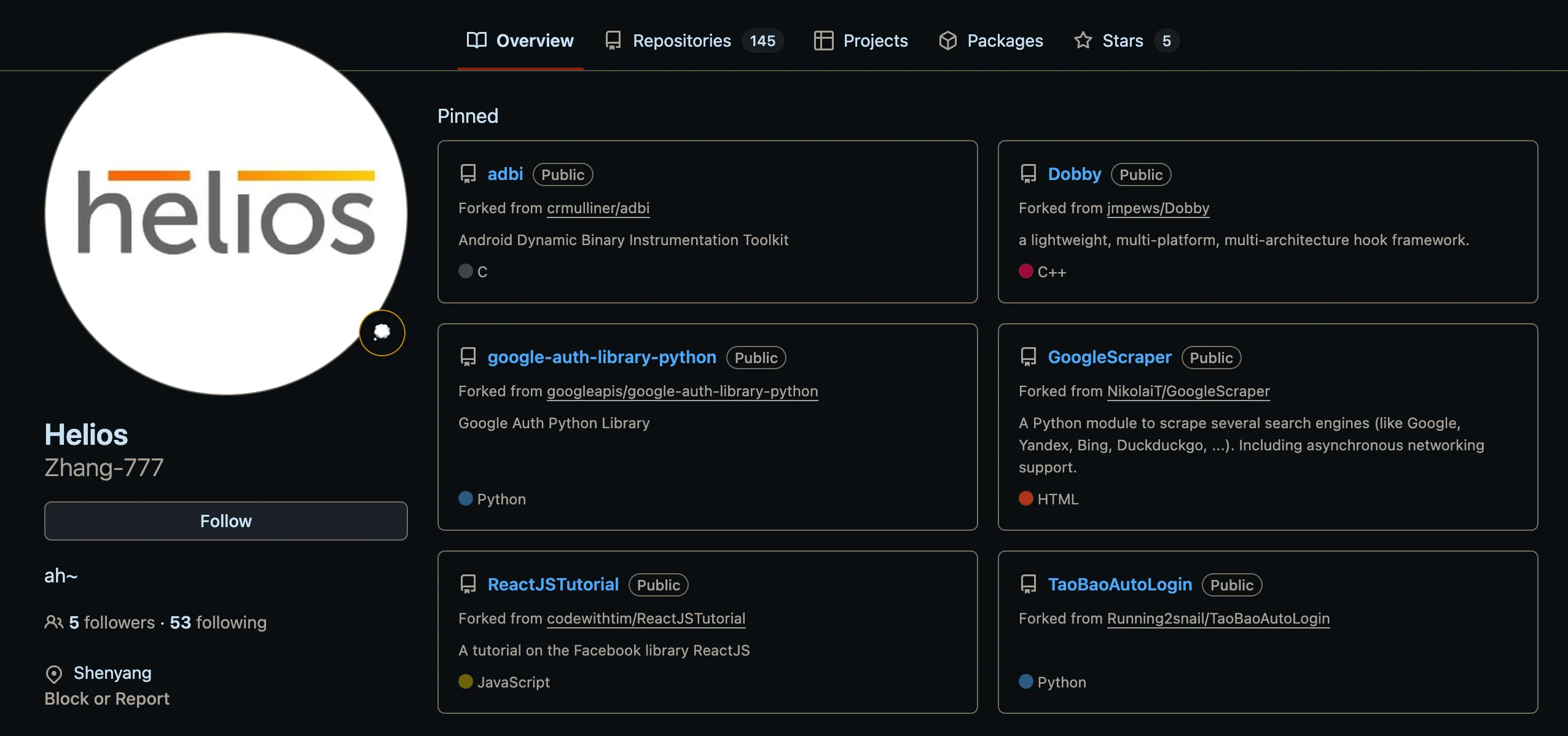
During initial analysis of the stealer logs, Helios' host stood out the most due to having applications such as IDA Pro Advanced, NoxPlayer (an Android emulator), and Telerik Fiddler installed. They also showed an interest in Cydia, iOS, and Android development. Their browser data listed reverse engineering as one of their skills and had visits to six different cybersecurity focused websites:
- - infosecinstitute[.]com
- - 52pojie[.]cn (Chinese android cracking and virus analysis forum)
- - ichunqiu[.]com (Chinese whitehat security forum)
- - pediy[.]com (Chinese exploit and vulnerability research)
- - pentester[.]land
- - ctdefense[.]com
We were unable to find any indications of Helios posing as a western based freelancer, and most of their account information either tied back to Shenyang, China or Japan. While we weren't able to find too much open source information on Helios, they're an interesting example of an IT Worker who could potentially be involved in offensive operations.
## Aiden Mori:
Out of the 5 sets of stealer logs, only one of them originates from outside of Khabarovsk. Showing an external IP that geolocates to Hong Kong, and having been infected in 2022, the autofill and password data paints a picture of an IT Worker heavily focused on blockchain and full stack development. There were 9 different personas observed, based in Ukraine, Singapore, Japan, the Netherlands, and Canada -- several of which were able to be tied back to freelancer profiles. An autofill item listed part of their work experience as working at a large Web3/NFT game that has been listed on several major news outlets. Autofill information also showed addresses that link back to a temple and Hainanese clan home in Singapore, a partial address most likely in Russia, and a home in Ontario, Canada.
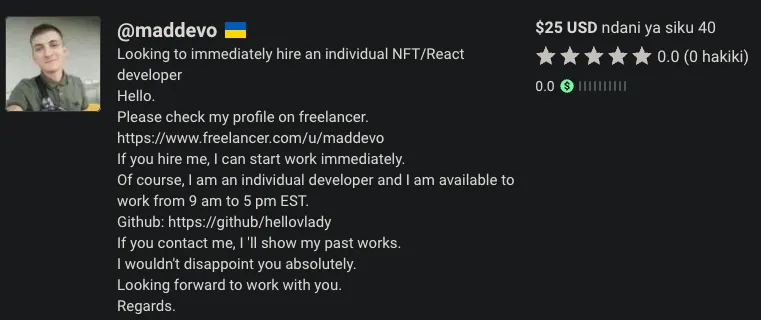
Most of Aiden's accounts appear to have been terminated or deleted since infection, though remnants of them still remain, as seen above. "Maddevo" was seen responding to hiring posts on a freelancer website for NFT and web design projects between 2022-2023. Another persona, that still appears to be active, led to a Blockchain developer who lists work experience as a founding team member of a fairly large crypto-backed job marketplace, a blockchain project focused on legal compliance, and a cryptocurrency investing platform. Their contact information included two different Skype VOIP numbers and a LinkedIn account which appears to have been terminated. One Github account found in the stealer logs, that initially appeared deleted, was found to be synced to a third-party website that led us to discover another active persona not found in the logs. This persona had a much larger online footprint and clearly put much more effort into appearing legitimate.
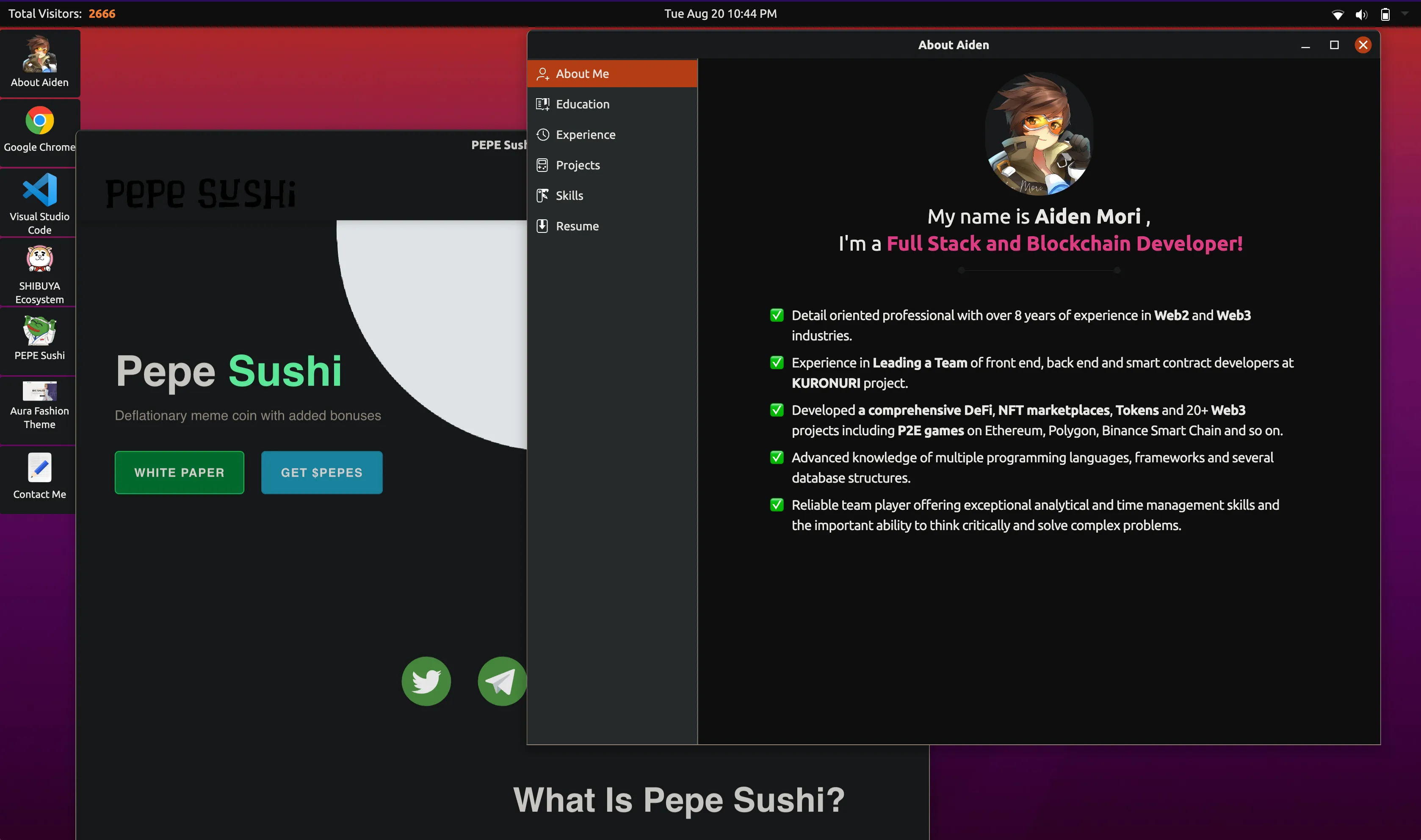
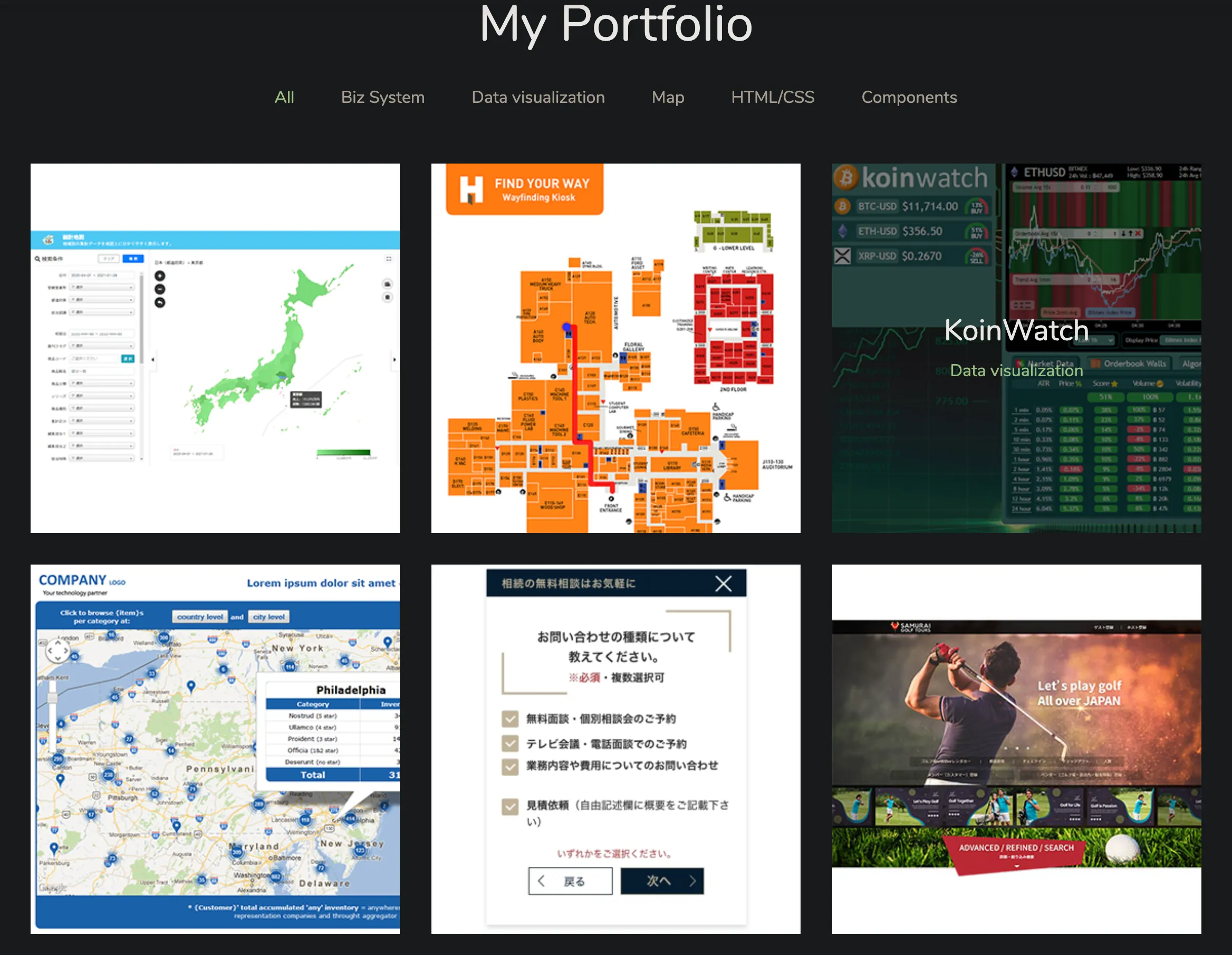
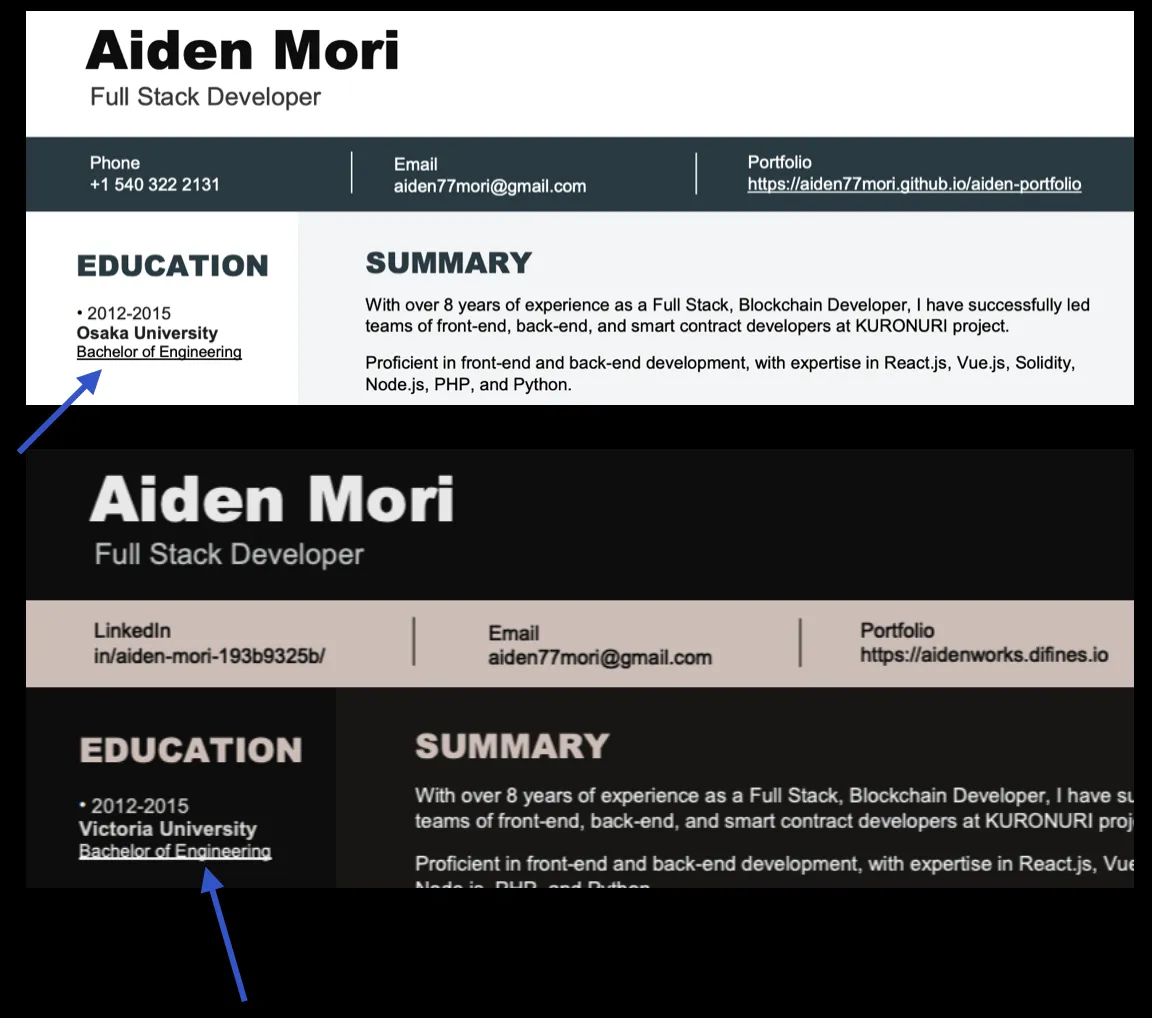
Now going by "Aiden77Mori" or "Aiden Mori", he has continued to advertise himself as a full stack and blockchain developer. His profiles all appear highly legitimate and well thought out, with a flashy portfolio site, and impressive resumes. Two versions of their resume were recovered, showing two common IT Worker indicators -- use of VOIP numbers and inconsistencies in education. One resume claimed that Aiden went to college in Tokyo while another claimed Sydney, Australia. Interestingly, Aiden also has a profile on Habr[.]ru, a Russian job marketplace where he lists smart contract development, Solidity, Web3, and Fullstack development as his areas of expertise.
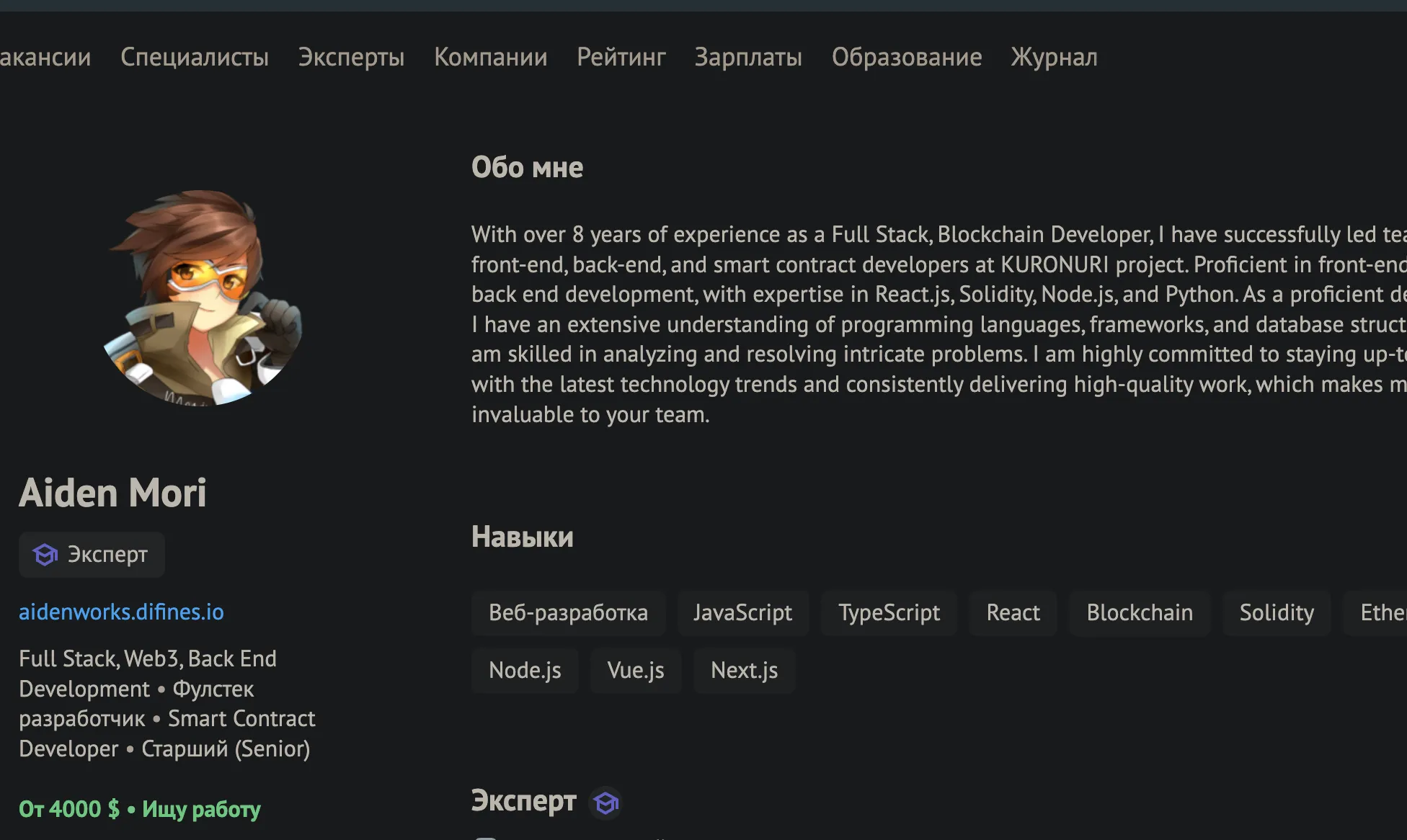
Aiden lists 52 projects on his portfolio site, including for two companies based in Australia, in the medical and real estate sectors, and a multitude of cryptocurrency projects ranging from news and media, to gaming platforms, and DeFi projects. At the time of writing, he currently sits as a cohort on a cryptocurrency media project. He appears to run the website difines[.]io which hosts several examples of his larger projects, such as FujiChat, which labels itself as an anonymous messenger application and advertises having a token listed on PancakeSwap. Aiden was also observed seeking investors for a project titled the "SHIBUYA Smart Ecosystem" that included a 79 page whitepaper. This whitepaper lists the project as planning to have features such as a decentralized crypto academy, an automated trading platform, and a freelancing app.

Another project he is involved in, called KURONURI, describes itself as a: "Hight quality Limo Rolls Royce despatch service" that includes NFT games. Looking at the team members for this project lists another one of personas found in the logs: "Vladyslav Pankhomenko".

Other projects of note include:
- - An anime-style AI girl that you can speak with called "Grok Bots"
- - A NFT marketplace/Play to earn game in the style of a Japanese RPG.
- - A fundraising and news platform with an NFT based around Koi fish
- - A crypto backed game called "Kingdom Infinite"
- - A blockchain-based lottery game
- - An AI video generator
- - A facial recognition app
- - A 3D storefront for e-commerce stores
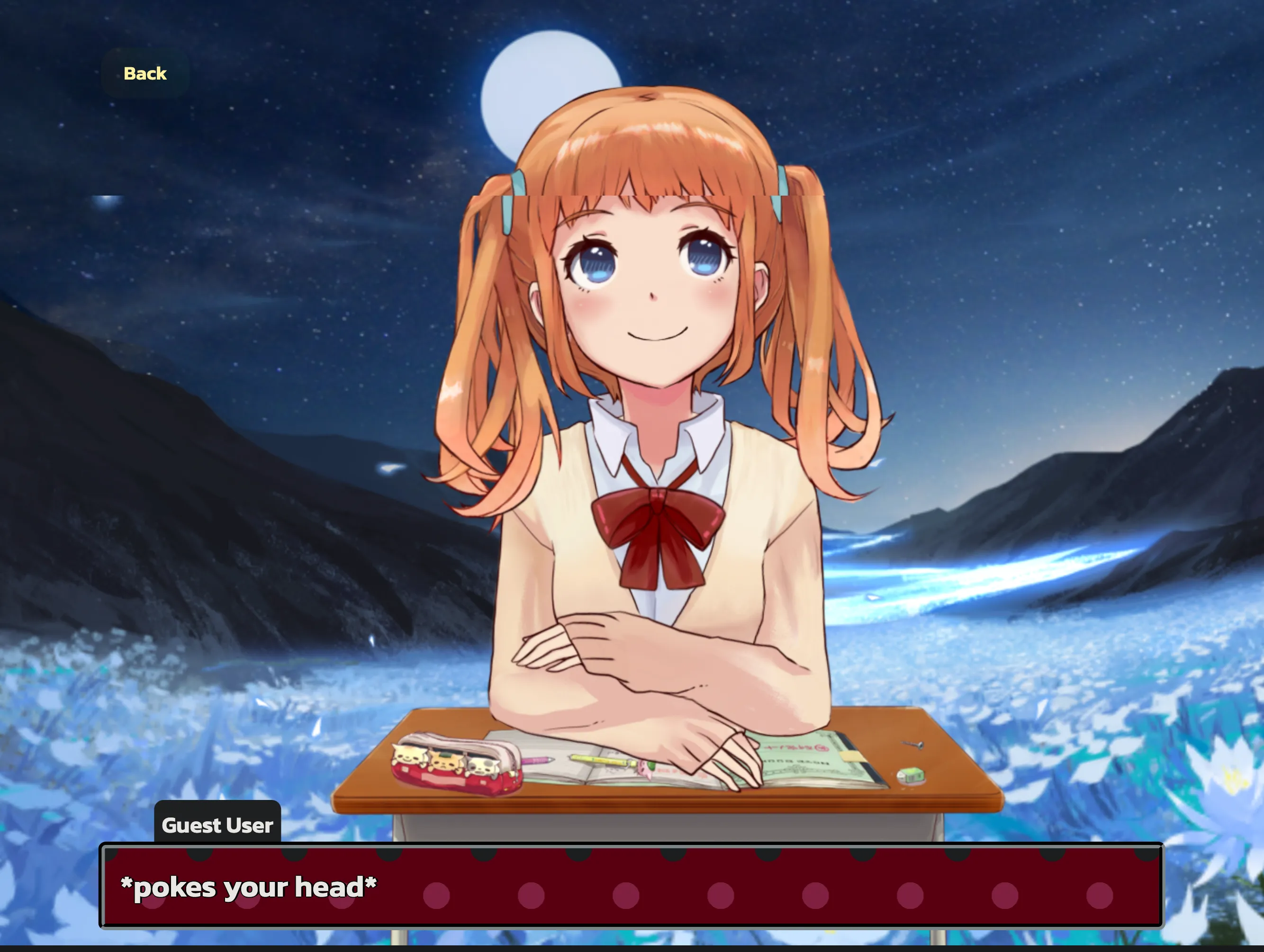
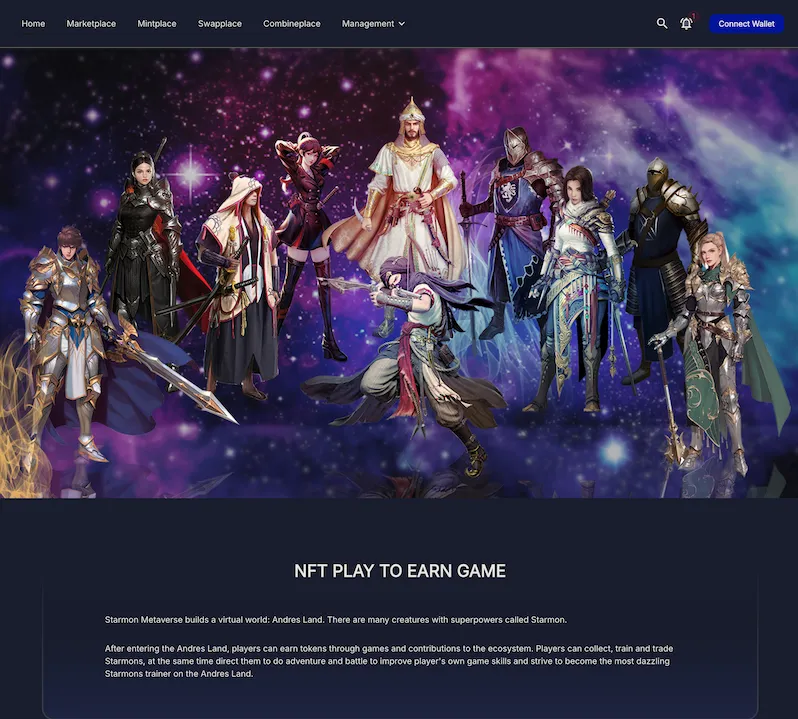
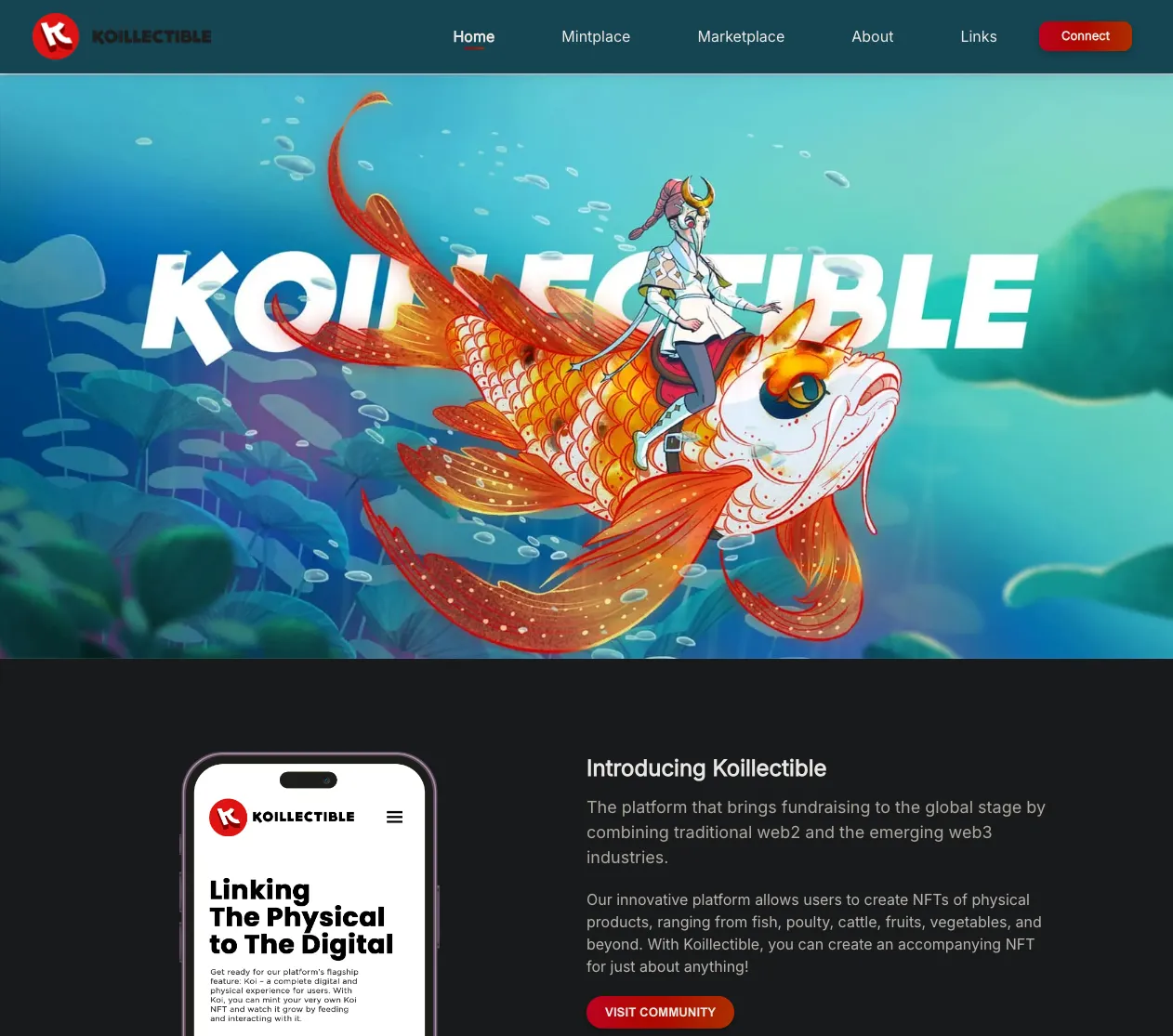

# Conclusion:
While a lot of data was excluded to protect impacted companies and projects, hopefully this post can shed more light on the IT Worker problem and help others with identifying them. Most of the stealer logs and personas covered showed evidence of having been employed at legitimate companies around the world, though we sadly do not have the means or time to verify this.
As a final note, we feel we should add that there are plenty more IT Worker stealer logs out there. IntelX showed at least 15-20 more sets of logs originating from the same IPs as these, some from as recent as September, 2024, that we were unable to source on our own. If you believe you have IT Worker logs and are willing to share or discuss more, feel free to contact us at chollima_group@proton.me.
References, and a select list of IOCs, are available below. More resources can be found in the "Resources" section of the site.
smartfox1203@gmail.com
codeknight0707@gmail.com
seniordev9726@outlook.com
anydev1103@gmail.com
fulldev114@outlook.com
masterdev1027@gmail.com
boriszhang1021@gmail.com
topdev1228@protonmail.com
hasan.musaj312@protonmail.com
toshyodev@outlook.com
slark0704@gmail.com
helios9116@outlook.com
cleanlake412@hotmail.com
masterdev1027@gmail.com
https://github.com/smartfox1203
https://github.com/hellovlady
https://github.com/fulldev317
https://github.com/Zhang-777

