# Introduction.
Around this time last year, Microsoft and Kaspersky released two reports on a campaign carried out by a previously unknown North Korean APT Group dubbed 'Moonstone Sleet'. This campaign was especially notable for it's use of a fake crypto game project called DeTankZone and the two chained Chromium zero days hosted on it's website.
After Kaspersky's later report on DeTankZone, we here at Chollima Group began looking into the "legitimate" mentioned called DefiTankLand. To our surprise, we identified a group of DPRK IT Workers that we clustered as BABYLONGROUP.
As we continued pivoting deeper into this cluster we identified that many members had previously worked on a huge cryptocurrency project on behalf of a shady company called ICICB (who we believe to be a front), that one of the non-DPRK members of the cluster runs the Chinese cybercrime market FreeCity, and an interesting connection between DeTankZone and an older IT Worker who previously operated out of Tanzania.
Although much remains unknown, the BABYLONGROUP cluster is quite large and has a fairly long history that fills a unique space in the larger IT Worker ecosystem. While the various individuals associated with this cluster all differ in their own ways, their unique collective character centres around being purely focused on web3/blockchain technologies and being self-starters in the sense of mainly being involved in their own self-created projects. Several members of this cluster have gone on to start their own projects where they functioned as CTOs and either created fake CEOs, or potentially recruited non-DPRK individuals to fill the positions.
Although it is clear that in the past many members of BABYLONGROUP operated closely with each other, we no longer believe this to be the case. We are mainly using this term to simplify documenting a large cluster of IT Workers who, at least previously, shared a common connection.
Let's dive in.
# In The Beginning There Was Tanks.
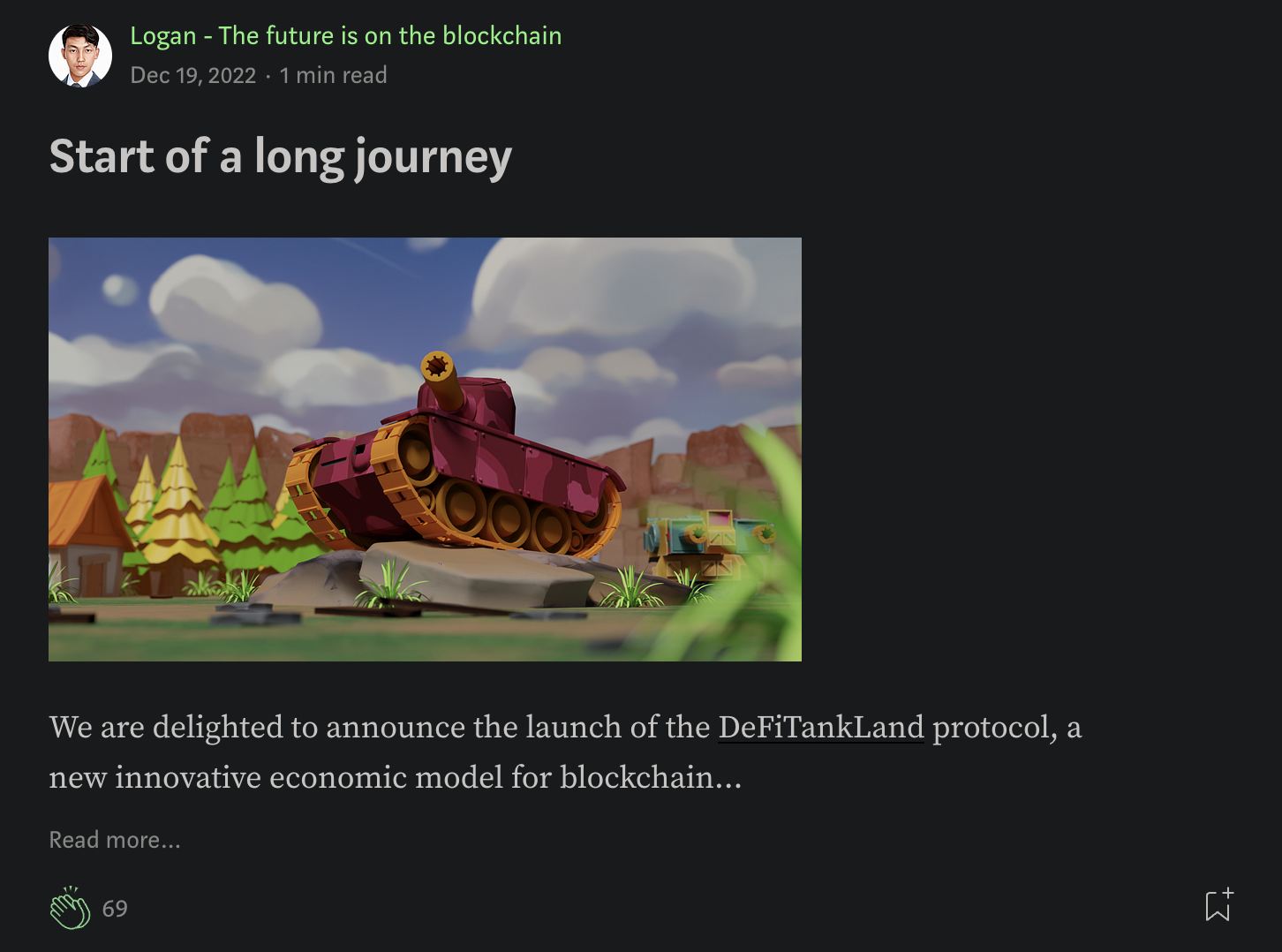
Kaspersky's mention of a legitimate predecessor to DeTankZone, called DefiTankLand brought us to the above Medium blog post by the project's CTO, Logan King. As far as we could tell, DefiTankLand first appeared towards the end of 2022 and claimed to be in active development until late 2024/early 2025 -- after the reporting from Kaspersky and Microsoft had come out.

Our interest piqued, we continued looking into Logan and quickly identified a number of data points that made us believe he was actually a North Korean IT Worker. This included his Github being used as a reference by a Ukranian freelancer named "Ivan Kovch", his use of different last names, his use of entirely different personas, and the fact that he was seen logging into his online profiles from IP space operated solely by North Korean entities.
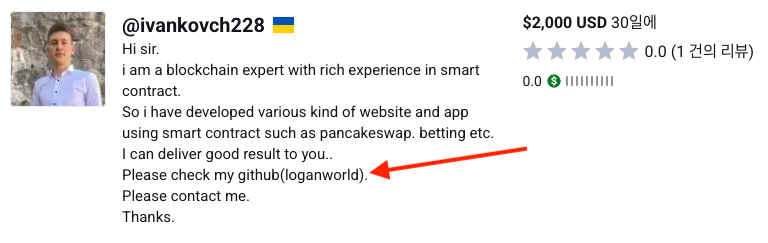
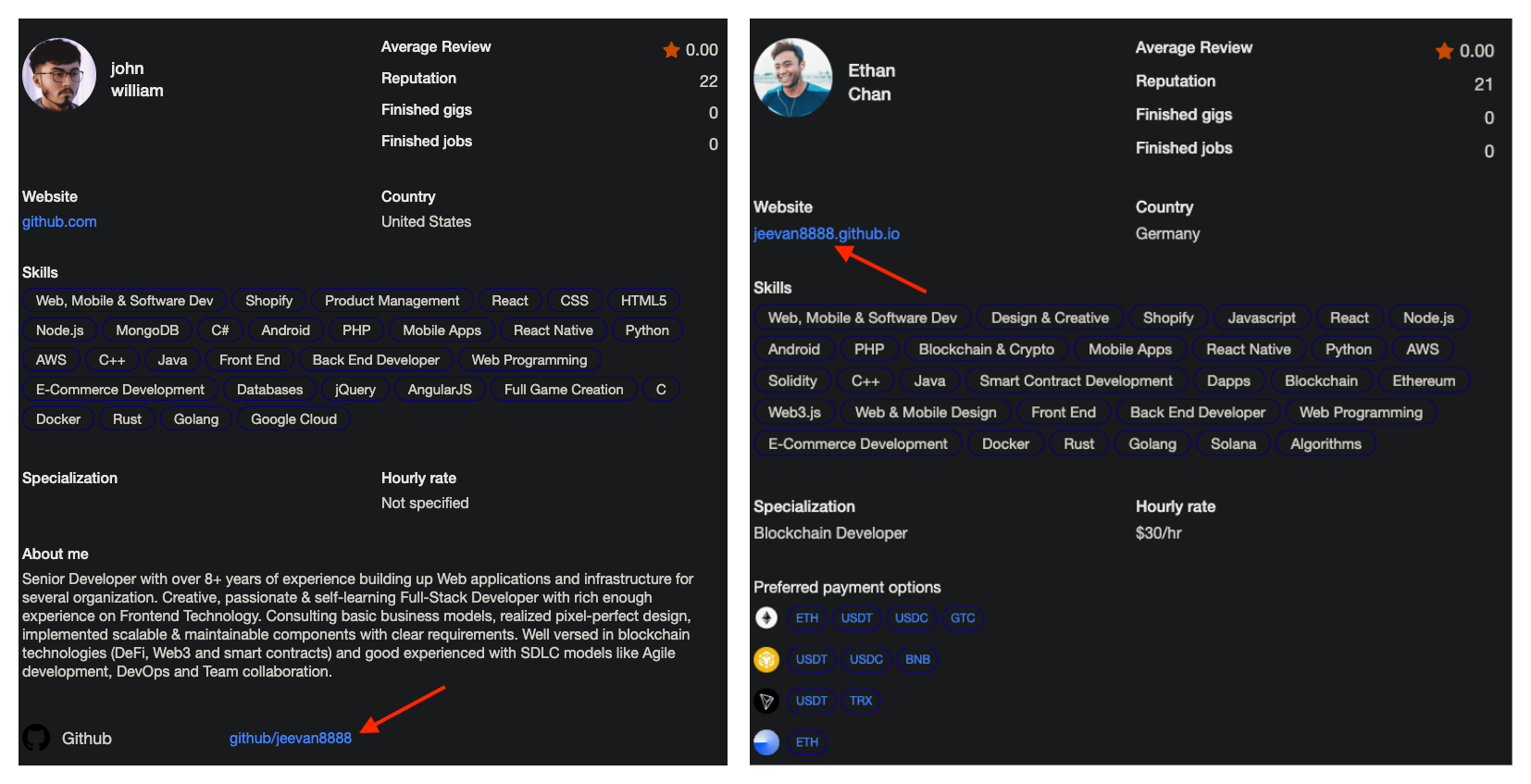
So what does this mean? Although we were unable to find a full list of the DefiTankLand team, we believe that the development team was primarily made up of DPRK IT Workers. While the DefiTankLand CEO Nabil Amrani has worked previously with Logan on other blockchain projects, we do not believe he is responsible for any of the development. This all means that the "legitimate" game behind Moonstone Sleet's DeTankZone was in fact developed by DPRK IT Workers, only to be later picked up and used by a North Korean APT Group.
# The Web Expands.
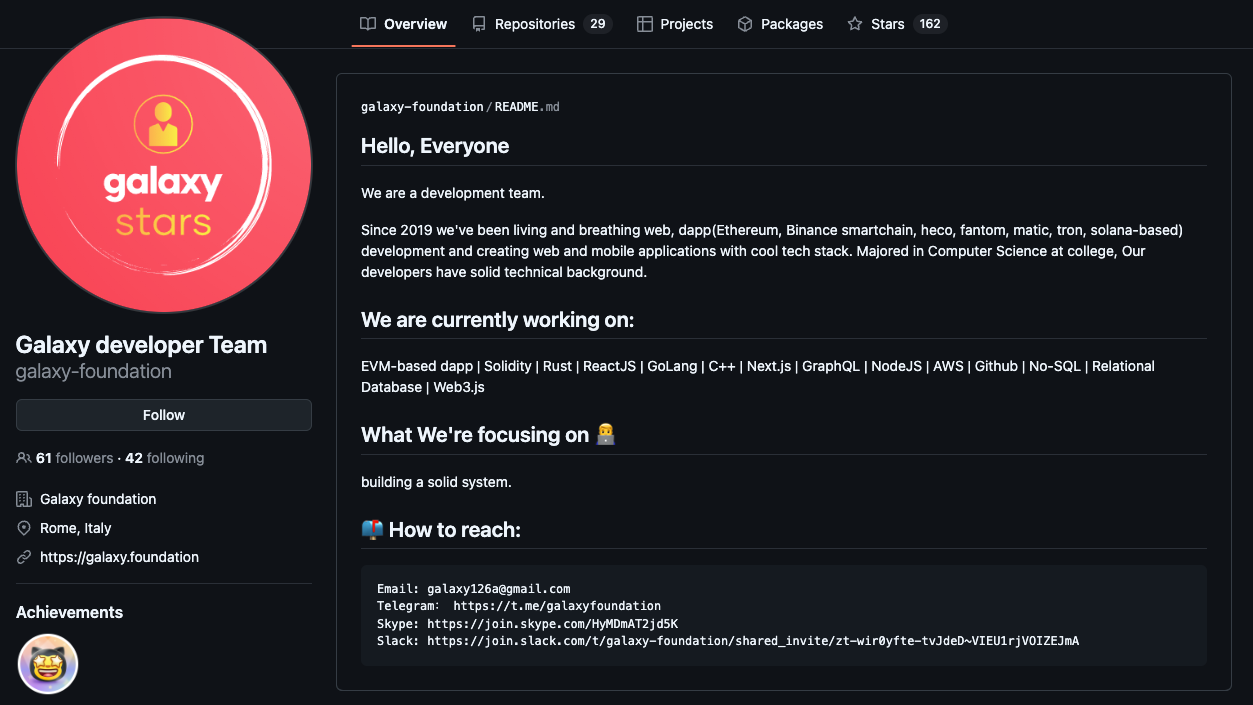
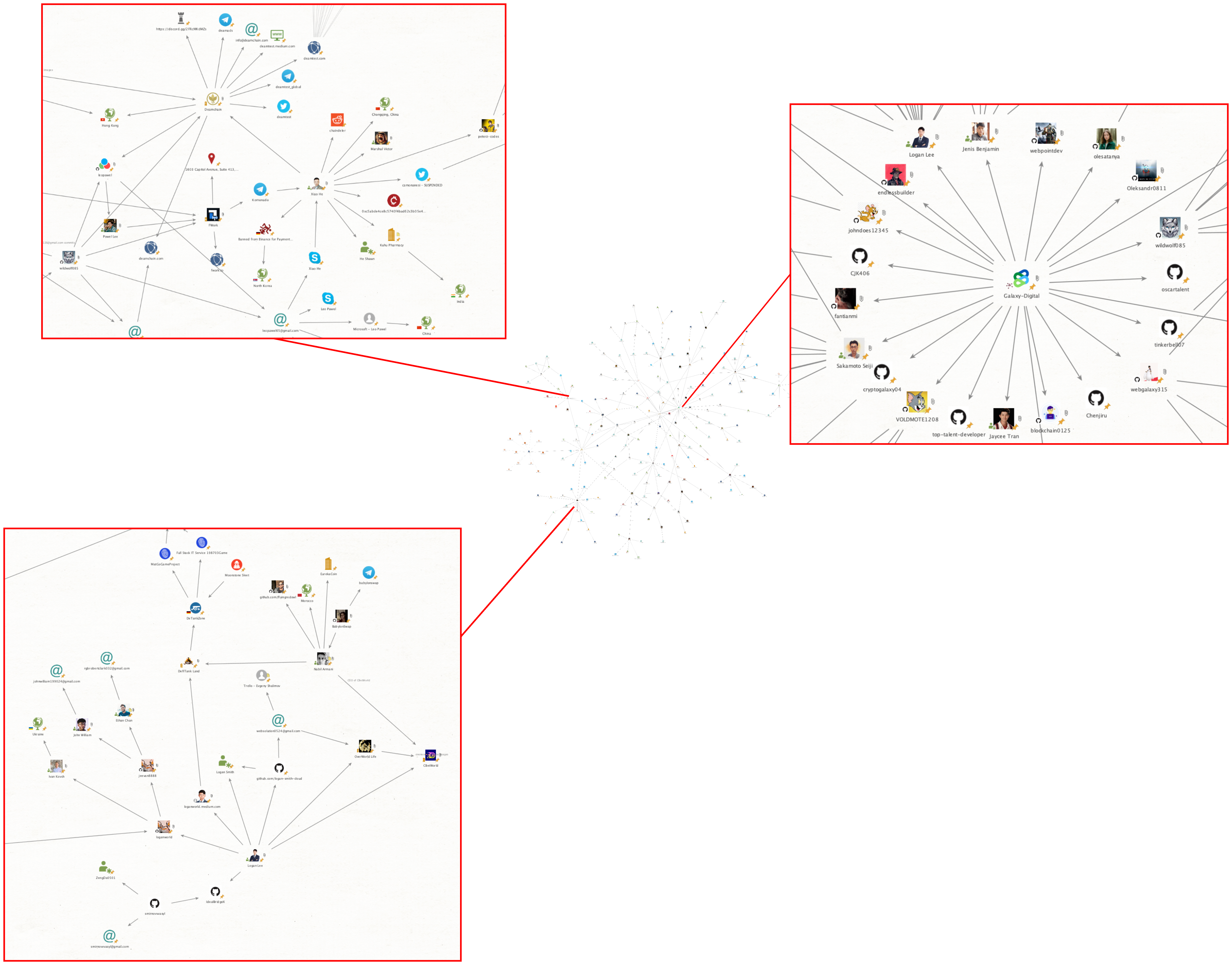
As we dug deeper, we noticed that many of these IT Workers were centered around a Github org called "Galaxy Foundation"/"Galaxy Digital" or BabylonSwap (a project associated with DefiTankLand). Although we believe that the vast majority of profiles associated with this account belong to DPRK IT Workers, we chose to only focus on a select few who shared overlaps in Github repo contents and work history. These accounts were mainly:
loganworld
smartdev-0205
newstable
jayceetran
webgalaxy315
sirbang
wildwolf085
leopawel
deamchain/deamtest
thomson0313
louistalent
endlessbuilder
VOLDMOTE1208
johndoes12345
bigben3918
icicbltd
Several of these accounts and their associated personas are quite interesting, such as promiselaw/smartdev0205 who typically goes by the names "Marcin Iwanski" or "Brent Jeremy", and runs a front company based out of Thailand called Prolocalize. Prolocalize claims to be a "digital globalization platform powered by deep technologies that enable enterprises to scale securely, efficiently, and across borders".
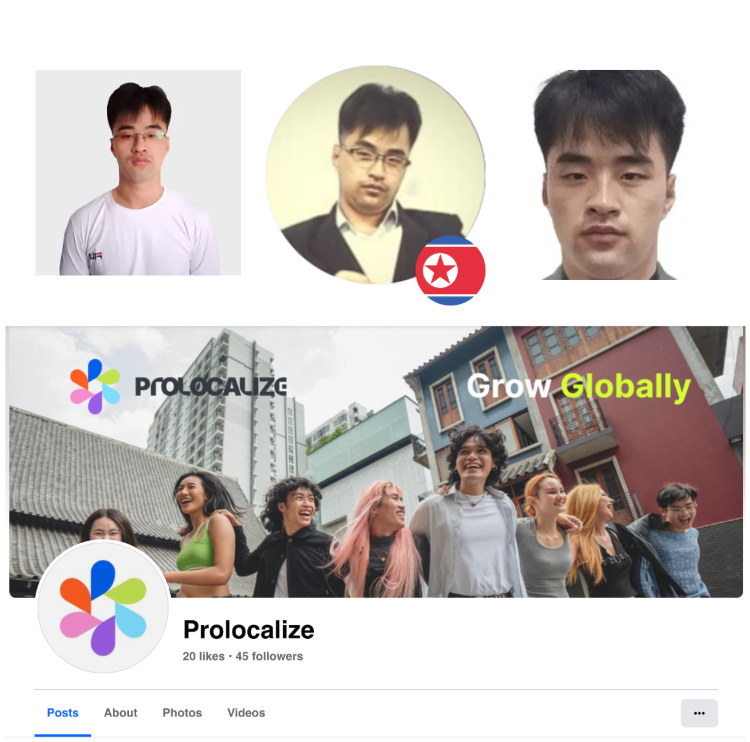
Then there is SirBang aka "Derek Miller", an IT Worker who we have only identified using this persona and who is solely focused on video game development. His Youtube channel features a video of Logan King and himself PvPing in a metaverse project they were developing that will be covered later. One of his freelancer profiles states: "Over my career, I have contributed to the development and launch of five games on consoles and Steam, one of which generated $5 million in monthly revenue".
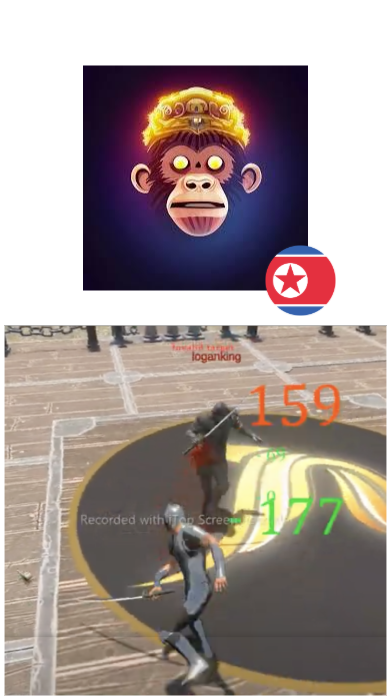
Thomas Anderson, in a vein similar to Logan was involved in creating his own project called "Crypto FIFA World" of which he was the CTO. He has also used the persona "Artem Stepanov" and frequently uses the numbers 0313 in his name.

Perhaps the most interesting member of this group was not North Korean at all, but a Chinese national using the handle wildwolf085 who appears to be directly working with the group. Although his real name is Xiao He, he most often uses the handle komonado or the name "Victor Marshal". In relation to his BABYLONGROUP connection, Xiao He has primarily worked on the projects DeamChain and FWork.io, both of which are web3 projects aimed at the freelancer market. Outside of his relationship to BABYLONGROUP, Xiao He is also an administrator of the Chinese cybercrime marketplace FreeCity Market under his handle "Komonado"(src), a crypto OTC/P2P broker who has had accounts shut down due to accusations of being affiliated with the DPRK, and is the purported owner of an Indian company called Kuhu Pharmacy that is involved in selling fake viagra and chinese herbal medicines on Telegram.
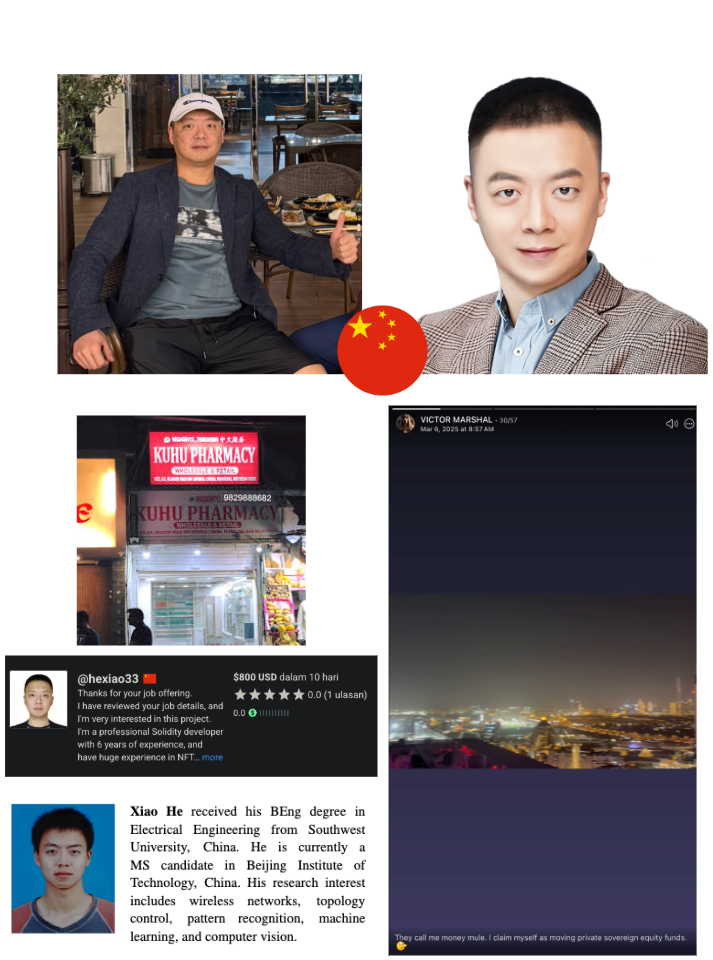
Xiao He also maintains freelancer profiles and appears to have published a research paper titled Traffic Load Distribution of Circular Sailing Routing in Dense Wireless Ad Hoc Networks while obtaining his Masters at the Beijing Institute of Technology. In a now deleted photo posted of himself, he appears to be at a Microsoft Research office in Hong Kong:

However, as we continued to dig through many of the BABYLONGROUP personas, we found that the most interesting element was what tied all of these personas together.
# The Dubai Connection.

As our investigation deepened, we noticed a trend that many of the BABYLONGROUP IT Workers had Github repos or work experience related to ATARI and something called "ICICB". While we knew what ATARI was, we found it quite odd that many of the accounts in this cluster decided to list the company, or whatever ICICB was, as experience. So we started searching.

Between 2020 and 2022 we discovered a plethora of very ambitious headlines discussing a Dubai based investment holding company called ICICB. Although we were unable to find anything new on the company, several articles stated that they were valued at $18 billion in February 2022 and had 114 offices in 26 different countries (or 220 offices in 110 countries, or 220 offices in 126 countries. It depends on which article you choose).
ICICB's claim to fame was their joint venture with ATARI on a multitude of interesting projects including, but not limited to: a blockchain called AtariChain, a metaverse game, AtariToken, and a collection of Atari-themed hotels that would be built in Dubai, Gibraltar, and Spain. This collaboration was surrounded by huge amounts of hype and marketing that resulted in both of the companies logos being projected onto the Burj Khalifa, an AtariChain Bugatti, billboards, ICICB winning a Tech Innovation Award, and plenty more:



Interestingly, and like many others, we couldn't find a single fully developed product made by ICICB, much information on its founders, or more than one of its hundreds of offices. Nevertheless, it appears that ICICB built a giant name for itself before Atari randomly terminated the joint venture and the company all but disappeared.

Still, the question remains: Why did these North Korean IT Workers have so many Github repos about ICICB and ATARI, and why did they list it on their resumes?
# "This isn't just some random, anonymous dev".
Although there were a host of different projects associated with the ICICB and ATARI joint venture, one of the more interesting ones was the Atari metaverse where players would be able to switch between historical eras and earn real world money. Although the project never appears to have come to fruition, we did excavate several videos featuring an awfully familiar username:
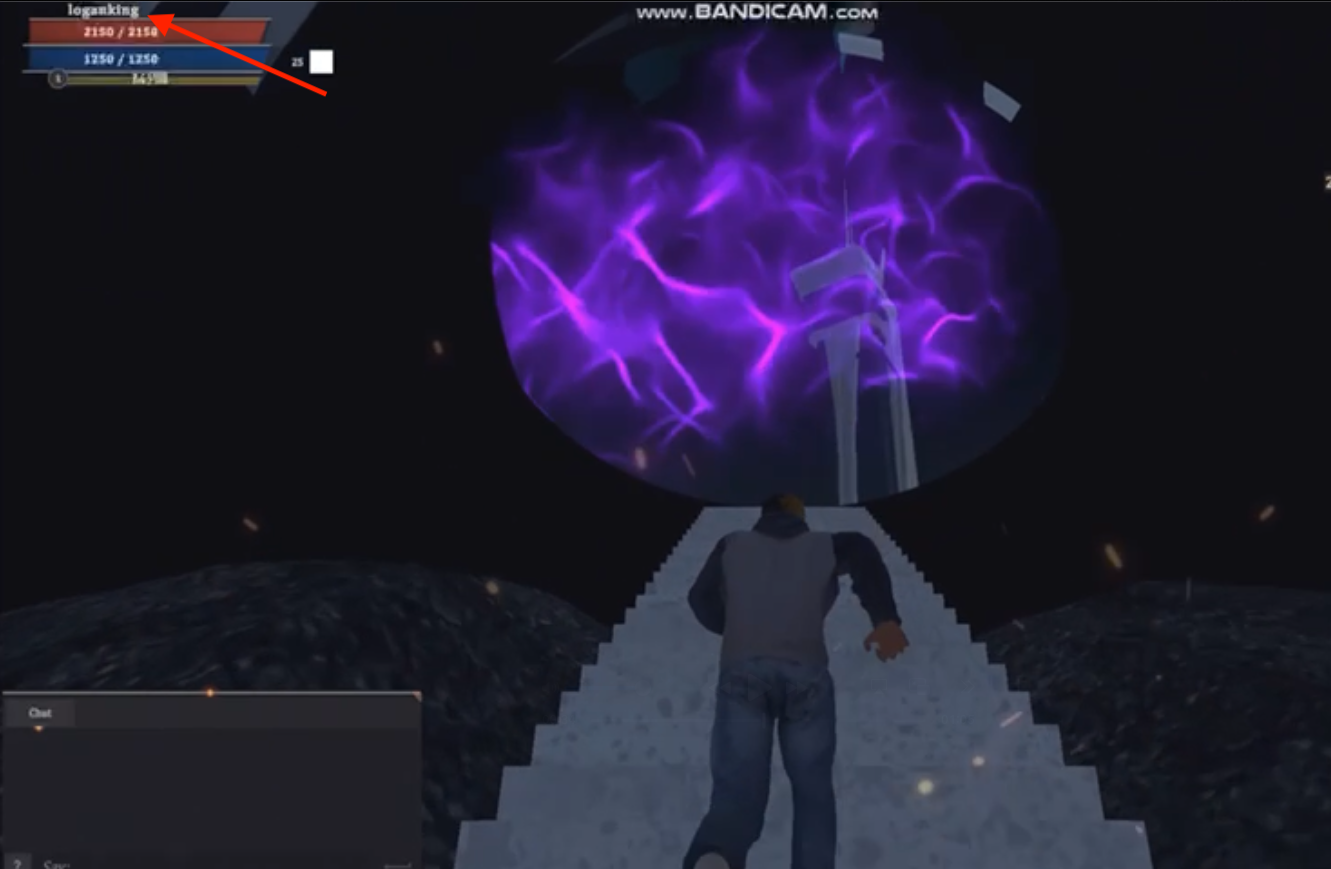
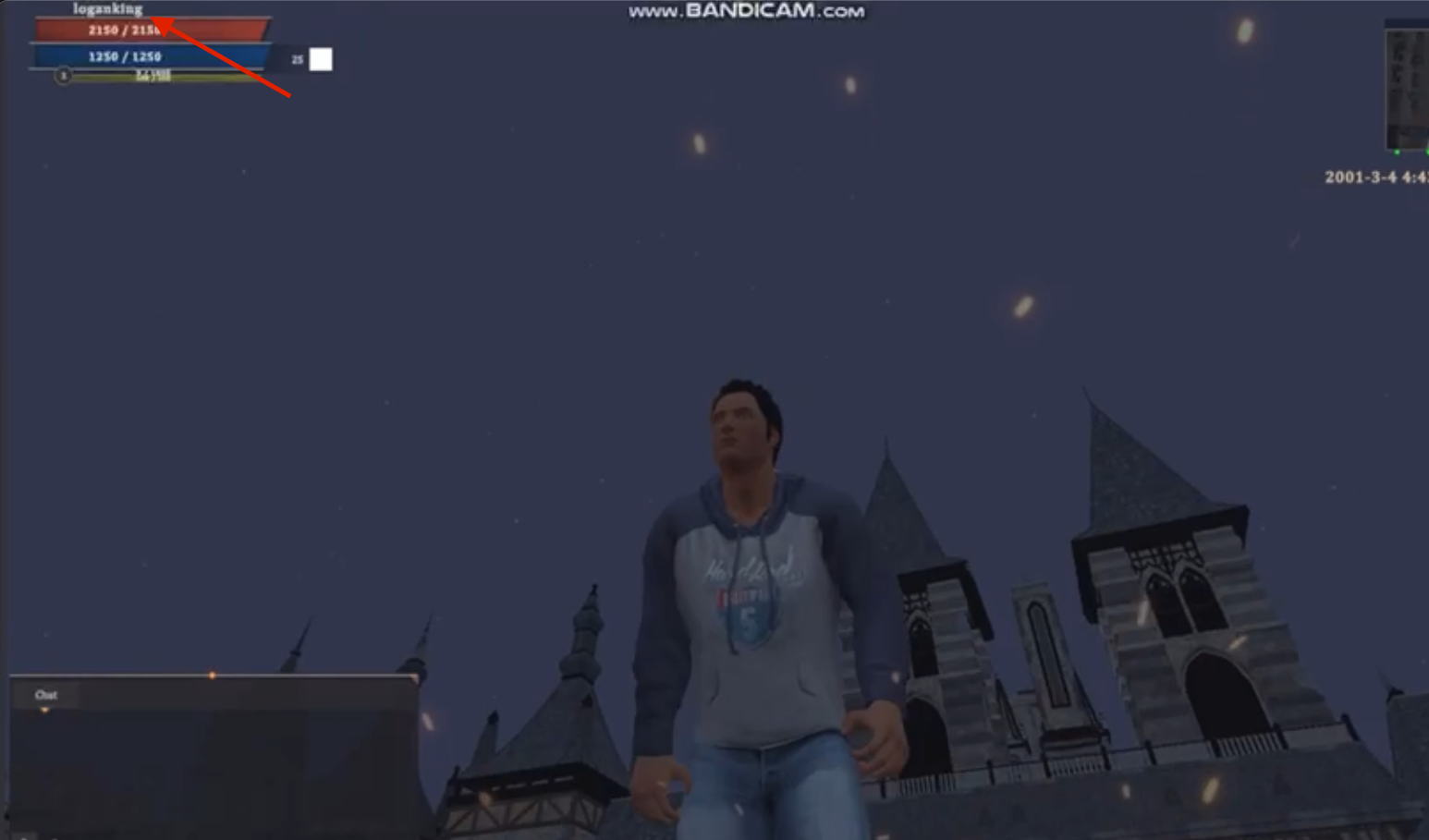
Nearly all of the official metaverse gameplay footage we found featured variations of Logan King's known aliases, which is also where the screenshot of SirBang and Logan King PVPing happens to originate from.
Due to this, and in conjunction with the other evidence highlighted above, it seems to us that the same group of North Korean IT Workers who made DefiTankLand also worked together years earlier on a project backed by ATARI while they were under the employment of a sketchy company who has since disappeared from the face of the earth.
This is not to mention that the price of ATARI Token was crushed before the public was even able to access the token, which some members of the community blamed on the dev team:
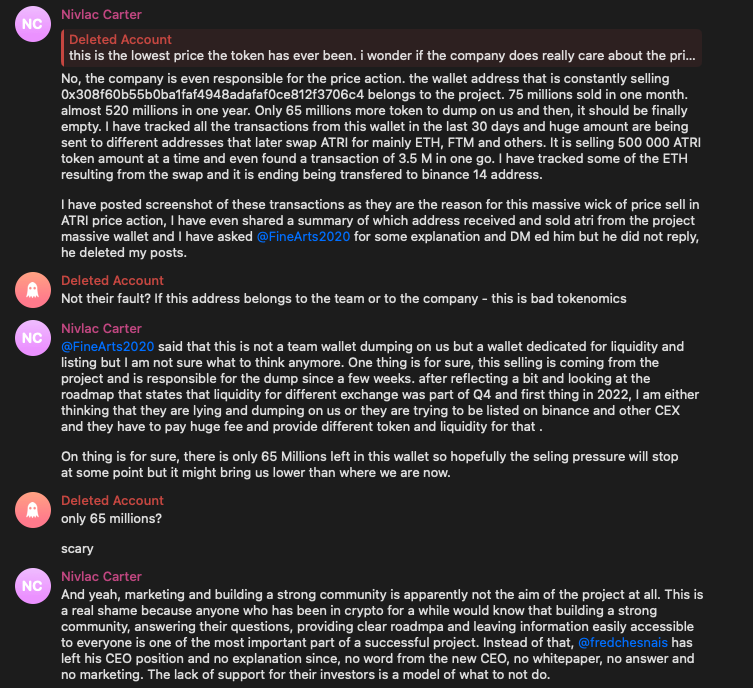
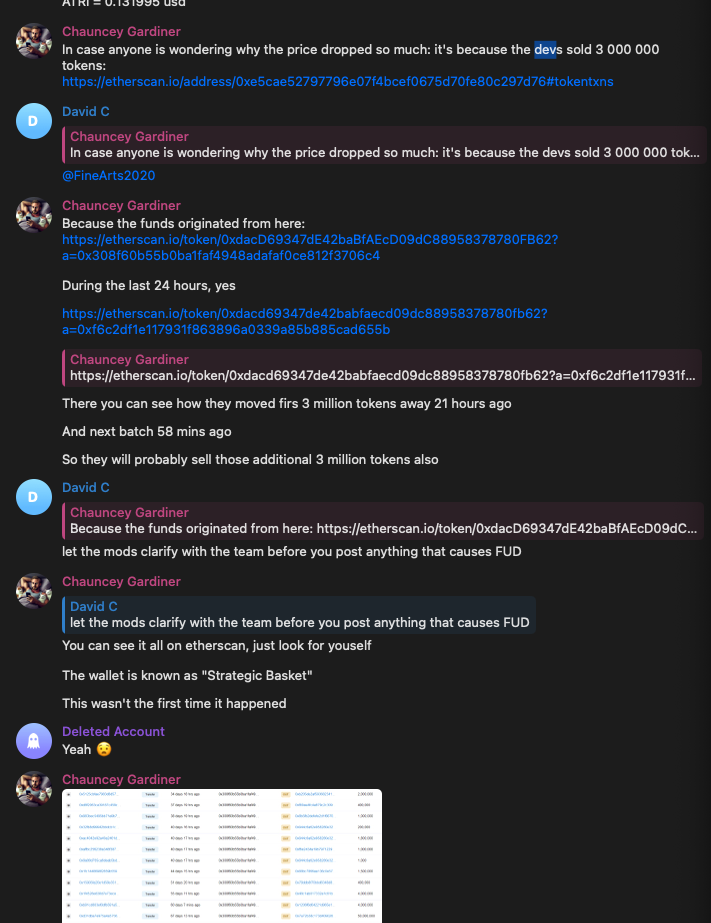
While we were unable to verify any of the claims regarding the price movements of the token, we feel it is important to note that many people who invested in the AtariChain project lost money not only due to the tokens crash, but also due to the unexpected termination of the joint venture.
# Closing the Loop.
A section of Kaspersky's blog on DeTankZone was dedicated to the game that victim's were invited to download on the site hosting the zero day. Kaspersky stated that the game had been compiled by the attackers and that the following AES Key and IV were used to encrypt the JSON data exchanged with api.detankzone[.]com:
Full Stack IT Service 198703Game
MatGoGameProject
During our investigation, we managed to identify a Github repo created by a user named sujan198703 that contained both of these strings and which appears to be an implementation of the Korean game "Go-Stop".
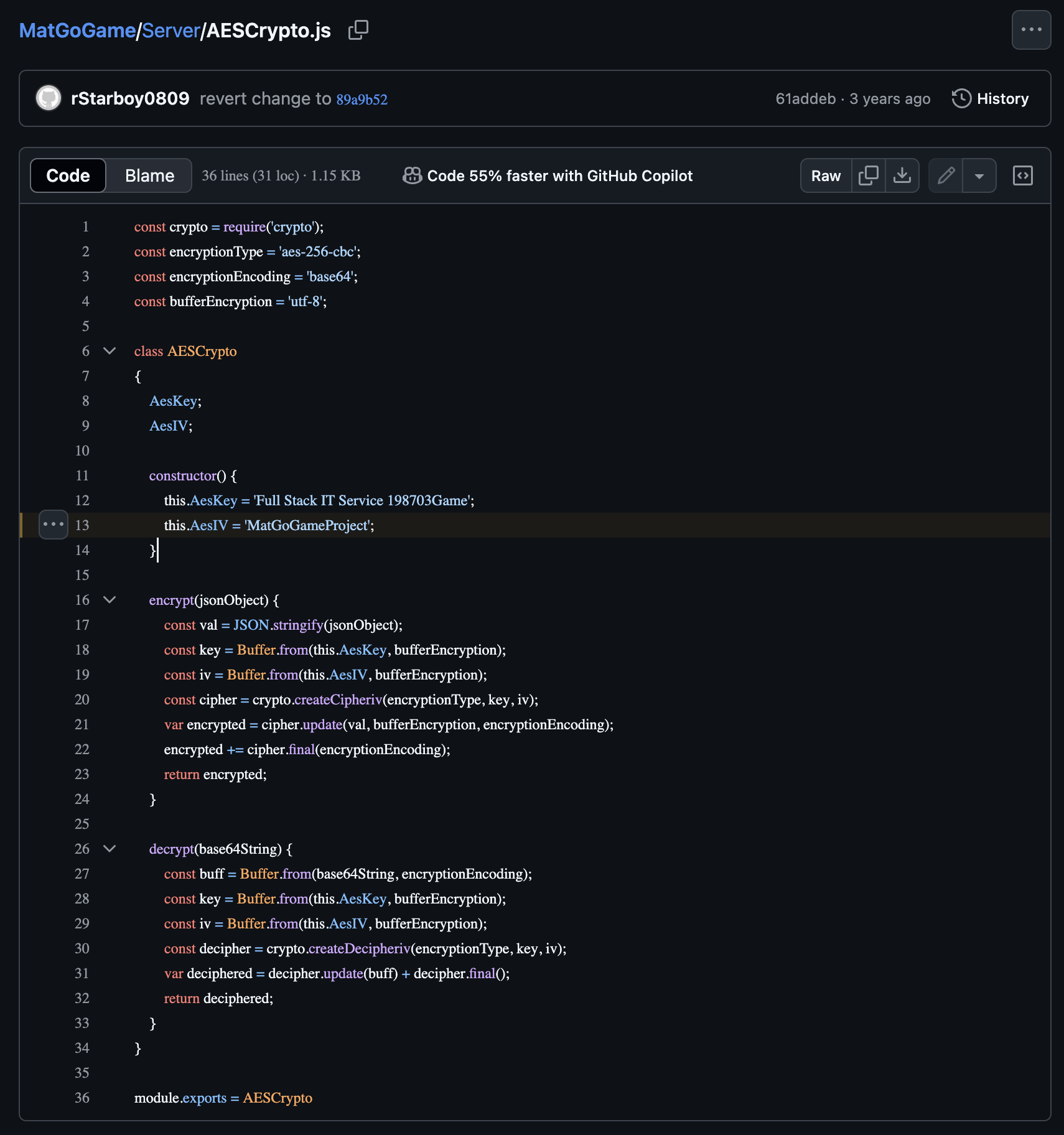
We found that this repo had been forked a number of times by accounts that we believe belonged to Logan King and PromiseLaw, specifically:
rStarboy0809
IlliaButenko
TopDeveloper0809
tDev0809
We also found that the creators account, sujan198703, was only two steps away from Logan and a host of other DPRK IT worker profiles, such as:
poprunner88 (James Gates)
lovelyBestDev (Happy)
Thomas-Kevin (YukioDev)
ChallengeDev210
OrdinalKing
techwizard210
wow-webmaster

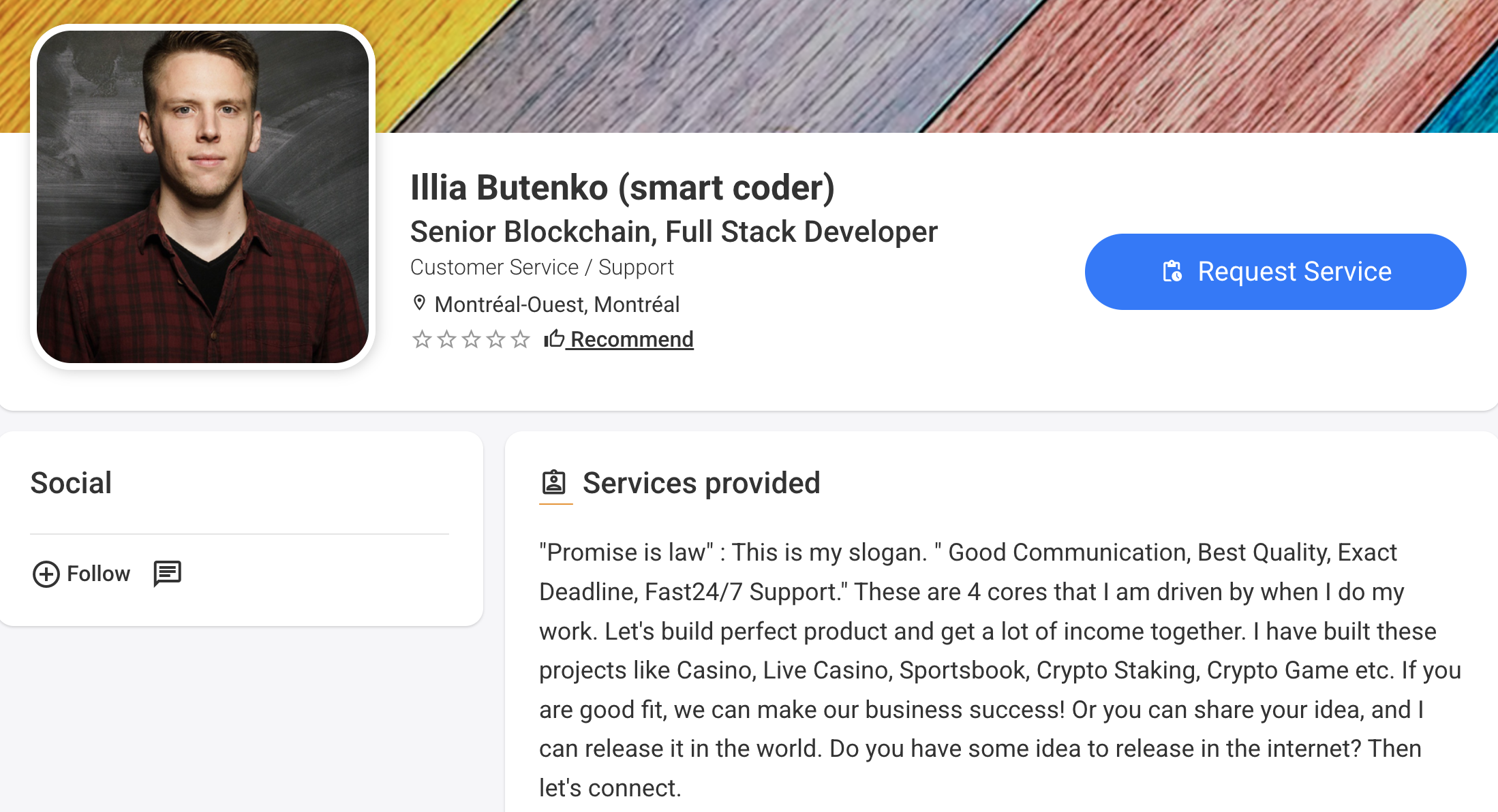
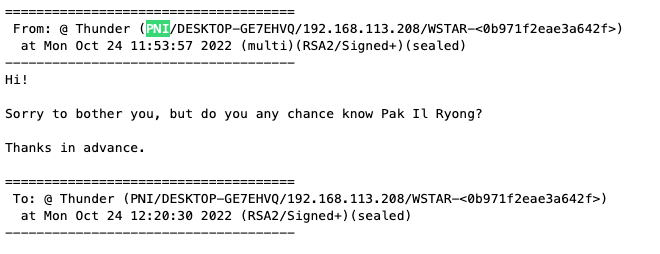
Although we are not entirely sure who operated the IlliaButenko account, we have high confidence that it was operated by a North Korean due to past login activity. Interestingly, Illia Butenko listed the organization PNI as part of his work experience on a Russian hiring website. While potentially just a coincidence, PNI was also one of the group names found in the leaked IP Messenger logs we have previously written about:
# Opening Another.

This all leaves us with one more question: Who is sujan198703?
Created in April 2022, the sujan198703 account has only used the email goldsea808@gmail.com. After some quick pivoting, we discover some interesting elements:
- This email is tied to a Trello account using the handle "JackDDK", which led us to a Youtube account of an AR/VR developer who appears to be based in China and uses Astrill VPN: https://www.youtube.com/@jackddk7187/videos
- It is tied to a Paypal account which uses a Chinese number as a hint.
goldsea808was a username of a CN-based freelancer on freelancer.com.goldsea808@gmail.comused the passworddlfska12in breach data.goldsea808@gmail.comis a sister account ofgoldsea808@yahoo.com
One of the first things we did was attempt to pivot off of the dlfska12 password. Doing a quick Google search, we noticed that almost the exact same password appeared as a comment on a Korean language forum post about the Squid game character "Oh Il-Nam", which asked "which password would he use?". We did not think much of this until we identified that this password is most commonly used by accounts that appeared to be of Korean origin, which is because dlfska on a Korean language keyboard comes out to "일남" or "Il Nam", a Korean name.
By now, we have identified an account that created a repo with Korean language artifacts, whose username, sujan198703, is most commonly of Indian origin, with an email whose connected accounts appear to originate from China, but who has previously used a password with a Korean name.
One additional pivot off of the goldsea808@yahoo.com account led us to a LinkedIn profile for An AR/VR developer/project manager based out of Jilin, China (an area that directly borders the DPRK) named Hailong Jin.

He will be the main focus of our next post.
# IOCs.
loganworld (Logan Lee/King/Smith):
---------------------------------------------
Current Project: Hogwarz, hogwarz[.]com
Emails:
loganlee002@gmail.com
loganworld002@gmail.com
akp707d@gmail.com
websolution0524@gmail.com
smirnovvvasyl@gmail.com
rgrobertclark032@gmail.com
johnwilliam199024@gmail.com
Github:
github.com/loganworld
github.com/logan-smith-cloud
github.com/jeevan8888
github.com/smirnovvvasyl
Telegram:
defiworld_dev
loganworld
logan_lee_c
Personas:
Logan Lee
Logan King
Logan Smith
Vasyl Smirnov
Ethan Chan
Leon Zhang
Evgeny Shalimov
upwork.com/freelancers/~014d511b5978bb9853
promiseislaw (Marcin Iwanski):
---------------------------------------------
Emails:
promseislaw@gmail.com
smartdevpro001@gmail.com
brentjeremynel@gmail.com
onetouch0525@gmail.com
kevinlee2821@gmail.com
leondragandevelop@gmail.com
eric2022412@gmail.com
ma.liguo@outlook.com
donatelo212dunccine@gmail.com
ernestpapyan@gmail.com
topsmartpro@prolocalize.com
yatsukalbert@outlook.com
talentdev610@gmail.com
leonpower123@outlook.com
oskardev0112@gmail.com
88yurchak@gmail.com
Github:
https://github.com/brent-jeremy
https://github.com/Smart-Dev-0205
https://github.com/talented-blockchain-dev
https://github.com/squirdev
https://github.com/pedrodiaz417
https://github.com/topsmartpro
Telegram:
smartdev19961
smartdev0205
trust0205
Discord:
Talented Blockchain#3570
Skype:
live:.cid.ffe8d0454926464f
Hiring Websites:
https://linkedin.com/in/promise-law
https://pl.linkedin.com/in/marcin-iwanski-b699b02b8
https://www.linkedin.com/in/brent-jeremy-47172b22a/
https://www.linkedin.com/in/brent-jeremy/
https://www.linkedin.com/in/liguo-ma-060077205
https://torre.ai/brentjeremynel?r=GLXbkZCc
https://www.guru.com/freelancers/brent-jeremy
https://web3.career/@marcin
Personas:
Brent Jeremy
Marcin Iwanski
Liguo Ma
Pirachat Chaiwongrote
newstable (Jaycee Tran/Sasuke Uchiha):
---------------------------------------------
Emails:
jayceetran.cool@gmail.com
special.galaxy26@gmail.com
potter0525james@gmail.com
zoelasa1111@gmail.com
it.galaxy.0315@gmail.com
sasuke031026@gmail.com
f99964995@gmail.com
Github:
https://github.com/newstable
https://github.com/webgalaxy315
https://github.com/nova-blockchain
https://github.com/jayceetran
https://github.com/zenggang315
https://github.com/sasuke031026
https://github.com/sasuke1026
https://github.com/sasukeuchiha
Telegram:
newstabled
Discord:
newstable
Skype:
live:.cid.f4e6d1509205ccdd
Hiring Websites:
https://www.linkedin.com/in/jaycee-tran-a2873230b/
Personas:
Jaycee Tran
Sasuke Uchiha
SirBang (Derek Miller):
---------------------------------------------
Emails:
derek.miller0003@gmail.com
derek.miller03@outlook.com
Github:
https://github.com/SirBang
Telegram:
DerekGameDev
Skype:
live:.cid.73d9933f3c8fe3e3
Hiring Websites:
https://www.guru.com/freelancers/derekgamedev/portfolio
https://www.fiverr.com/derekmiller03
https://laborx.com/freelancers/users/id328992
Other:
https://www.youtube.com/@DerekMiller-h8m
https://twitter.com/DerekMillerDev
https://derekgamedev.com
Personas:
Derek Miller
Xiao He:
---------------------------------------------
Emails:
hexiao33@gmail.com
hexiao33@yahoo.com
hexiao33@hotmail.com
hexiao33@mail.ru
hexiao31@mail.ru
hexiao32@mail.ru
hexiao34@mail.ru
4445313@qq.com
peterzhou0802@gmail.com
kawabatakyo0922@outlook.com
jamesybarra114@gmail.com
jo.hnceballos0716@gmail.com
hughnolan88@gmail.com
deliminallimited.ws@outlook.com
galaxy85126@gmail.com
leopawel65@gmail.com
Github:
https://github.com/peterz-codes
https://github.com/camonanesi
https://github.com/wildwolf085
https://github.com/leopawel
Telegram:
komonado
Hiring Websites:
https://www.lancers.jp/profile/camonanesi
https://www.peopleperhour.com/freelancer/technology-programming/xiao-he-fullstack-web-developer-blockchain-vxqqqxj
Personas:
Xiao He
He Shawn
Peter Zhou
James Ybarra
Leo Pawel
Powel Lee
Wallet:
0xC5ABDE4CE8C5740F4bad6C3B05E4Da31d229659
Others:
---------------------------------------------
IPs:
45.126.3.252
188.43.136.0/24
Emails:
topdeveloper01234@gmail.com
bigben199551@gmail.com
realhardworkingdeveloper@gmail.com
thomasanderson19960313@gmail.com
davidsuzuki51@gmail.com
toptalent48@gmail.com
alexstepan0209@gmail.com
kkopbusiness1213@gmail.com
blockchain4webdev@gmail.com
HighleyHilmaU@gmail.com
yemelyan.yevdokimov.domain1121@gmail.com
qiqq-ps@eclipso.eu
illia.butenko89@gmail.com
ddksniper@gmail.com
intellichain555@gmail.com
salbu15154@gmail.com
goldsea808@gmail.com
goldsea808@yahoo.com
alexstepan0209@gmail.com
jamesybarra114@gmail.com
mrsteevtvw418@gmail.com
toptalent48@gmail.com
ichiro@0xlancerlab.com
hanssuperdev1026@gmail.com
hansjkiller1026@outlook.com
tomasjakson44@gmail.com
ssch26802@gmail.com
williamh8930@gmail.com
Github:
thomson0313
fullstackdev8681
louistalent
galaxy-foundation
galaxydigital
TopDeveloper0809
IlliaButenko
johnhoang-star
techsavvyninja
intellichain555
pedrodiaz417
zkbusiness
chainoneer
sujan198703
alexiva0806
poprunner88
wow-webmaster
techwizard210
lovelyBestDev
Thomas-Kebin
ChallengeDev210
OrdinalKing
devlegend524
cryptodev524
alexstepan0209
kvenus-uj
suzukidavid
john741672
webcat882
lgamingdev1
rustsol114
maestro418
rizzolib
endlessbuilder
smile0307
topclever
webpointdev
crackdev01
devsirius51
devsirius5001
Discord:
thomson_0313
loganworld
loganlee002
seagod351
newstable
_codex0313
marketingconsult
anime_lover06827
olesatanya
cysho0105
benjamin_0105
overworldlife.com
Wallets:
0xA9C429B9469D9462A1f2C3a52e149512F87F5094 - Logan/Smirnovvasyl
0x9e051782754e1ED01C2800a820b9F742b38aceA0 - newstable
Organizations/Projects:
---------------------------------------------
ICICB
Kuhu Pharmacy
DeamTest/DeamChain
FWork.io
Kunzig Consulting
DELIMINAL LIMITED
github.com/Youth-Group
Crypto-FIFA-World
GADA Finance
BrothersCommunity
Prolocalize
CBetWorld
OverWorldLife
OpenPetWorld
DefiTankLand
DeTankZone
Babylonswap
0xlancerlab.com
Hogwarz

