# Introduction.
Recently some members of Chollima Group came across an open Google Drive folder owned by a North Korean IT Worker. The drive folder contained identity documents and resumes for an Iranian developer and 5 other personas, Payoneer/Paypal transaction info, a small database file of notes, a .log file, and a screenshot of an individual testing their webcam:

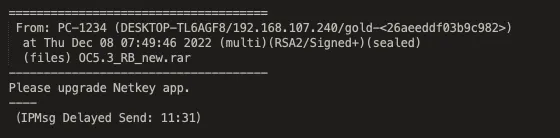
As we began to look through this folder, we noticed that the .log file was actually chat logs spanning between late 2022 and early 2023. Although we were at first uncertain of what application they originated from, as we continued to read through them we began to notice some key things that captured our full attention:
- The participants in these chats appeared to be involved in software development and freelancing, often collaborating on projects.
- The chat logs seemed to originate from an application called IP Messenger for Win, that facilitates chatting on a local network (and is also popular amongst North Koreans).
- Several of the files shared in the logs had filenames that matched those we have seen previously associated with two North Korean applications: NetKey and OConnect.
- Some messages specifically referenced individuals attending Kim Chaek University and from Chongjin, both places in the DPRK.
After analyzing these logs further, we believe that they almost certainly originate from inside a network used by North Korean IT Workers. There are roughly 500 individual messages sent between the IT Worker who originally uploaded them and 100 different hosts on the network.
Though much remains uncertain, these chat logs do provide some very interesting insight into how IT Workers operate and allow us to get a small glimpse into their lives. We have tried to bring attention to the most interesting points and answer the questions that immediately popped into our heads, while not making this post too overbearing.
Once we understood what we were looking at, we made a concerted effort to hunt for other IP Messenger for Win logs, but were unable to find any. In any case, the logs discussed below will always be available here in full: LOGS
# Understanding the Format.
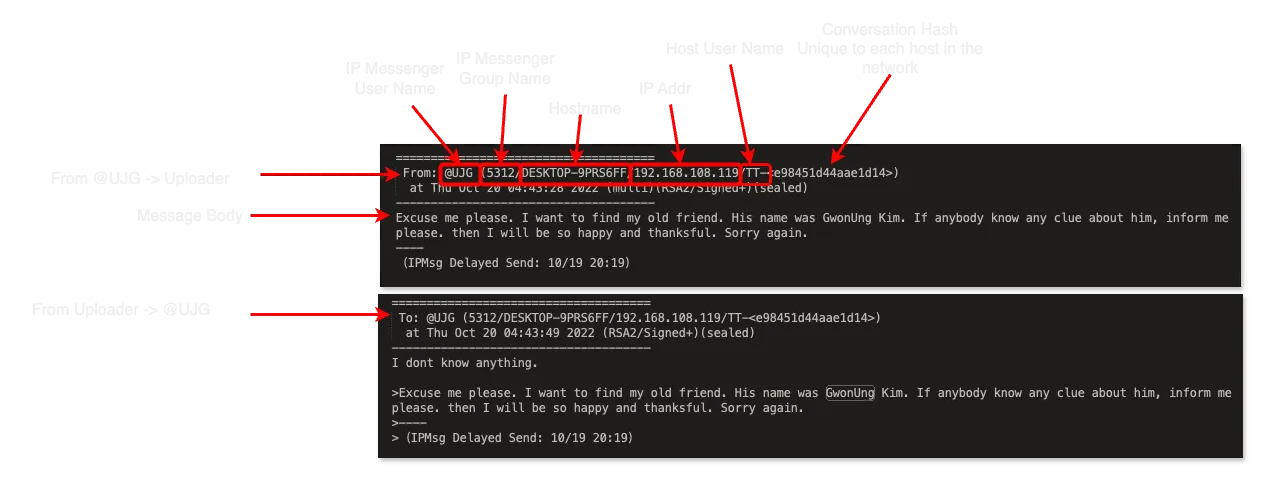
Looking at these chat logs was initially confusing for us because the application they originate from, IP Messenger, is not very well known. The most important thing to understand is that these chat logs are essentially private direct messages between the IT Worker who uploaded them, and other IT Workers in the same LAN network. All messages include a From: or To: indicating that either the uploader is receiving the message, or sending it himself.
IP Messenger allows you to send messages to a group or to the entire network, but there are primarily just direct messages present in the logs.
Another important item to note is that the user info carries some interesting elements that we have laid out below. One of these is the IP Messenger Group Name which is set by the user themselves.
# Location.
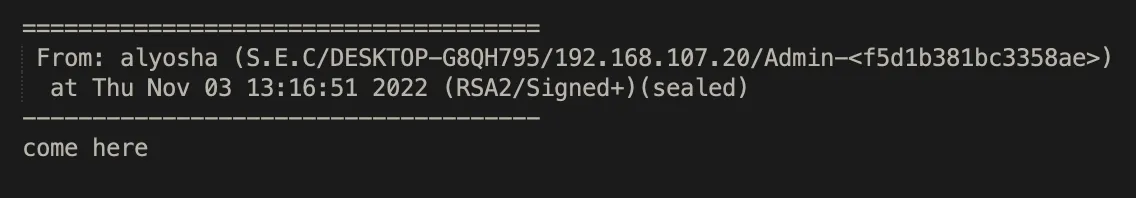
The first question that came to mind as we read through these logs was: where are these IT Workers located? While we do know that North Korean IT workers are often based in countries like Russia, China, and Laos, there is sadly no clear indication as to the physical location of the workers in these logs. However, certain messages indicate that some of the workers are likely to be in the same location or shared facility. The uploader of the logs frequently receives messages from individuals on other teams asking him to come to them, as seen below:
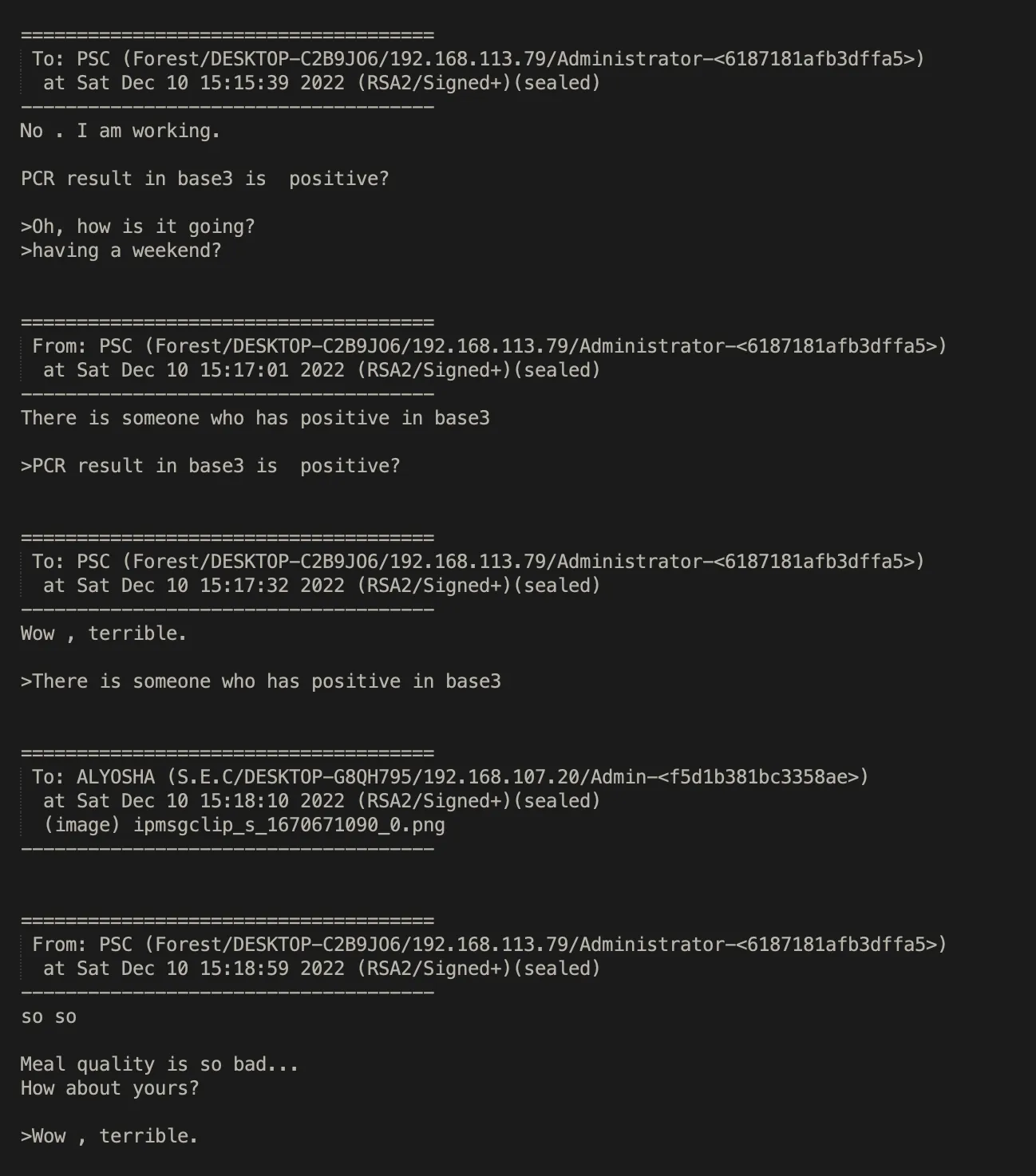
In one of the direct messages with an IT Worker using the handle PSC, the uploader asks about someone testing positive for COVID at a "base3". This leads us to believe that some of the physical locations these workers are at may be a part of a larger, organized network. Some of our past investigations have identified clusters that that this would be consistent with, while others appear to be more frequently on the move and living out of large, rented domociles.
# Businessmen for a Common Cause.
While IT Workers tend to be characterized as a single force working towards generating revenue for the regime, they also seem to operate in sort of mini-economy of their own, where the selling of jobs, device access, and personas is potentially commonplace.
Although we saw much more sharing than we did selling, on several occasions different workers opted to sell their extra jobs or appeared to be renting out services. One such example is below, where we can see dolphin putting up a job for sale:
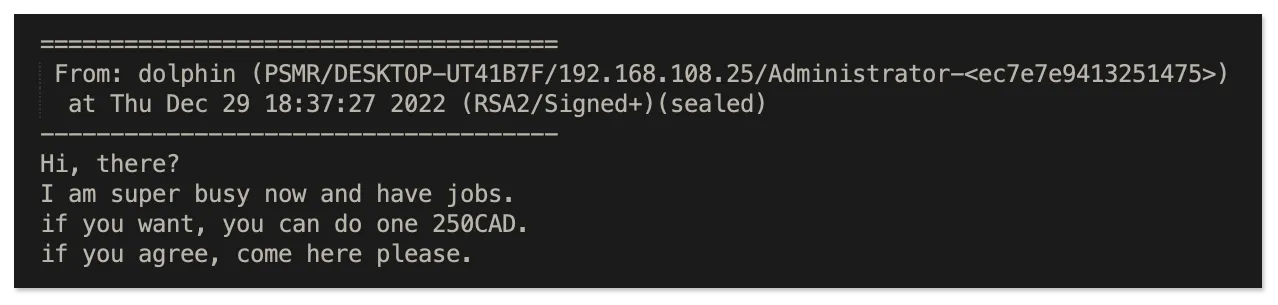
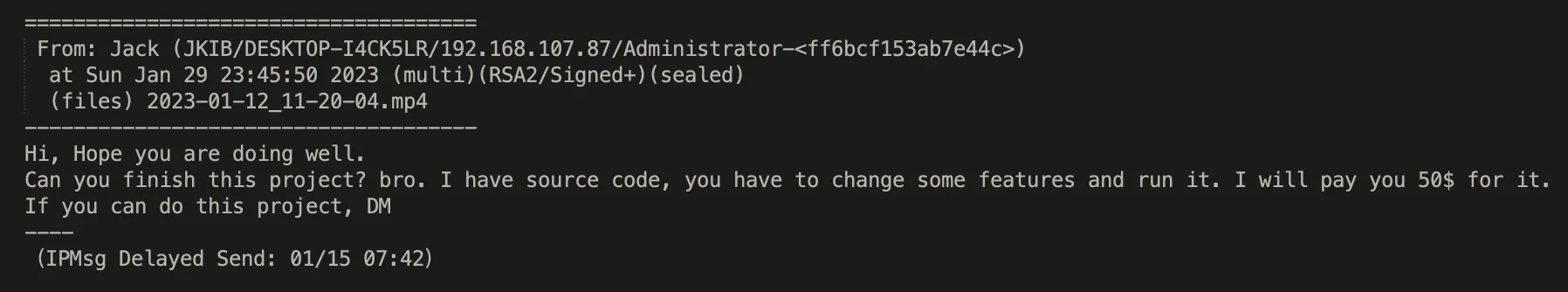
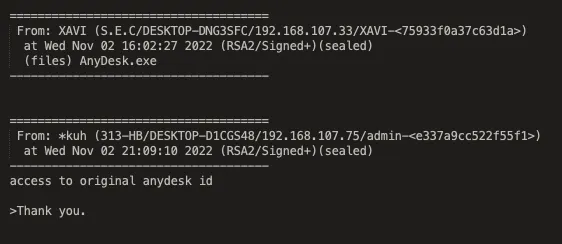
Another IT Worker, *kuh, who frequently interacts with the uploader, seems to have been renting accounts or a persona to the uploader. This includes AnyDesk access to a laptop run by a facilitator named Marko. The uploader does not seem to be in contact with Marko and always needs to go through *kuh if anything goes wrong.
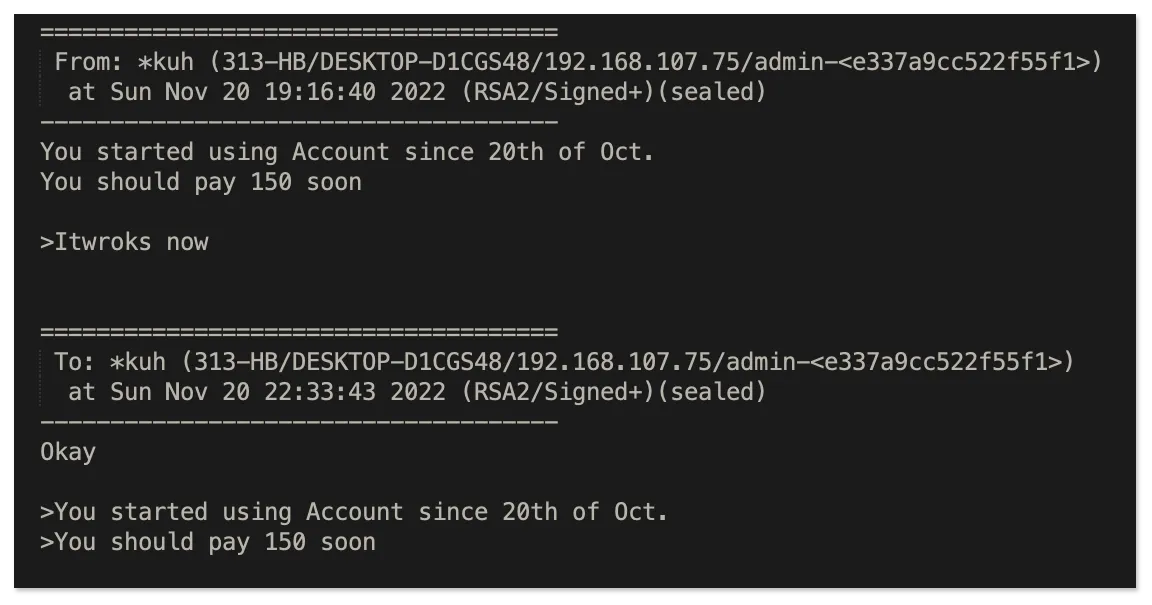
It is also possible that both the uploader and *kuh are renting services from the facilitator, Marko. In the past we have identified IT Workers using private services based out of Serbia that provide all infrastructure and documents needed to acquire jobs at Western Companies.
In the case that the selling of accounts and personas is a widespread practice, it may explain why we sometimes see one persona associated with a few different individuals.
# I'm Looking for Someone.
A large number of chat messages seemed to be focused on finding old acquaintances. These messages gave us the first real confirmation of where these chat logs were from, since they specifically listed Kim Chaek University of Technology (Spelled as Kimchak) and Chongjin (the third largest city in North Korea).
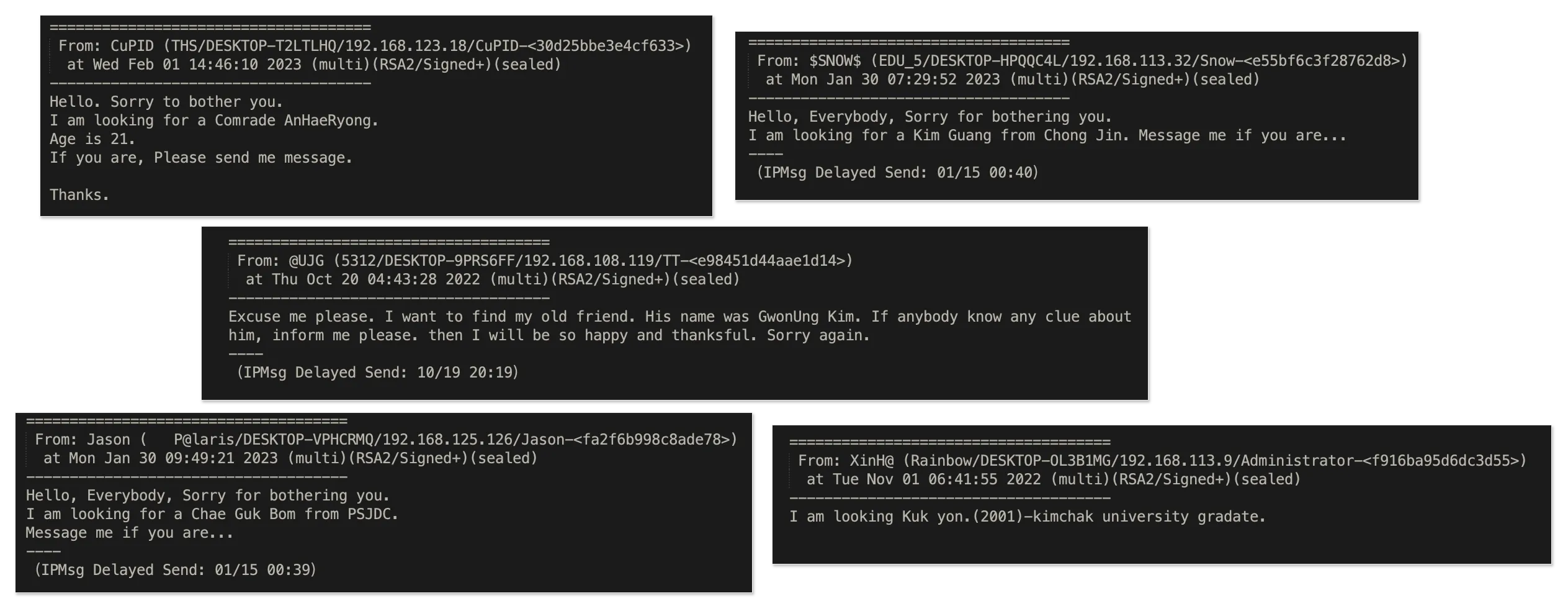
While this above messages may seem strange to outsiders, North Koreans seem to frequently lose contact with each other due to relocations and government mandated work orders. The novel Without You, There is No Us, based on the experience of a Western teacher working at North Korea's PUST Technical College, also touched on this multiple times due to her student's frequent complaints about missing their friends. There are two other subsets of the "I'm looking for someone" messages: those looking for specific usernames/account holders, and those looking for individuals "from" a set of numbers.
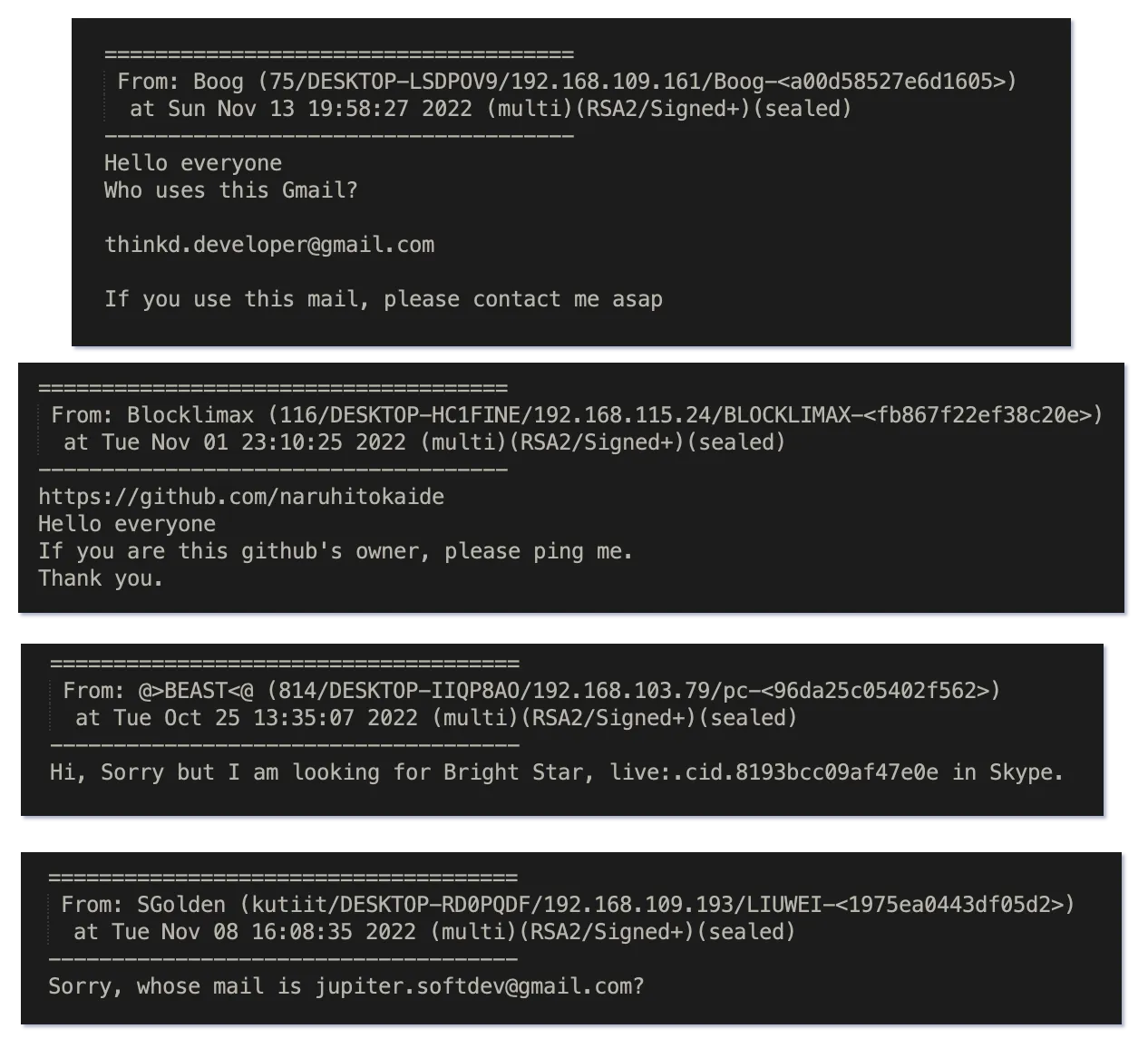
What makes these asks interesting is that Naruhito Kaide, shown above, is a known DPRK IT Worker. Since it's not really obvious how they are coming across these accounts, it begs the question of whether or not they're keeping track of accounts or are identifying themselves in the wild somehow.
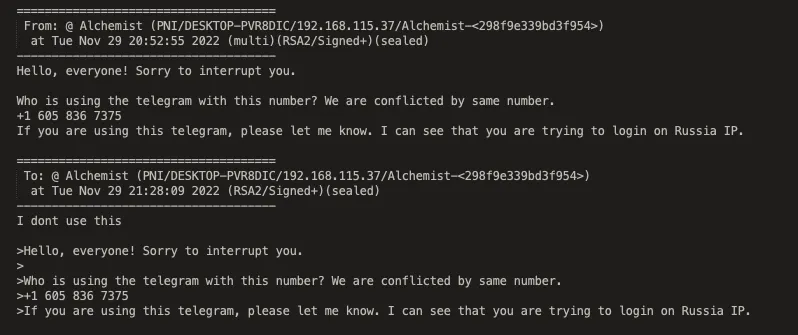
In the above chat message, Alchemist even asks specifically about a TextNow VOIP number via a multicast message. We found this to be quite odd unless there is some sort of central account sharing repository.
Finally, there are two more messages in the chats specifically looking for people from/in
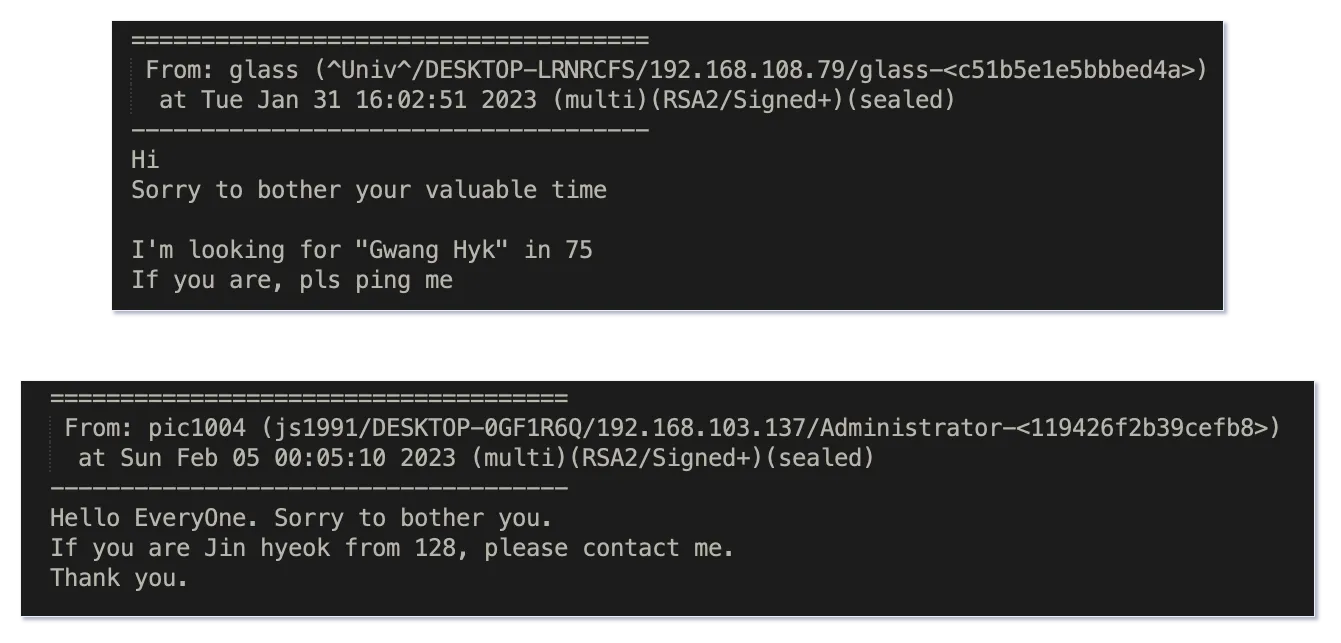
# Internet Access.
These chat logs sadly do not provide a clear picture of the workers' internet access. While they obviously have an internal network, which seems to include a CounterStrike server, there is some ambiguity about whether or not they can access the global internet.
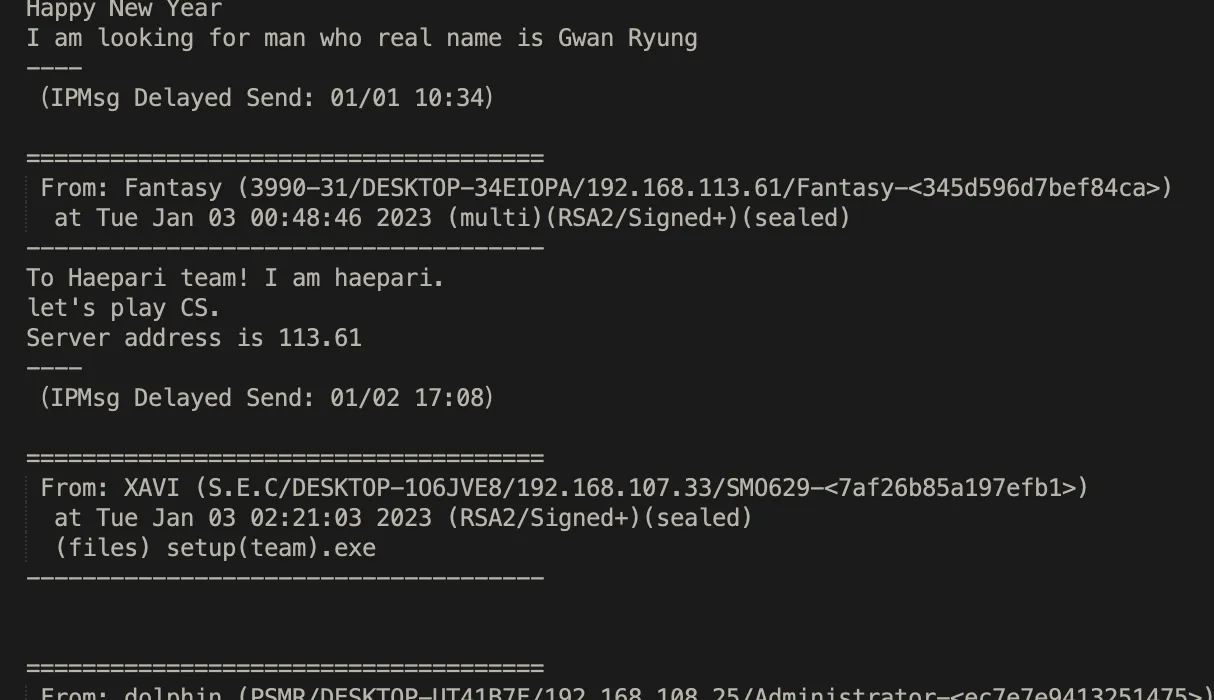
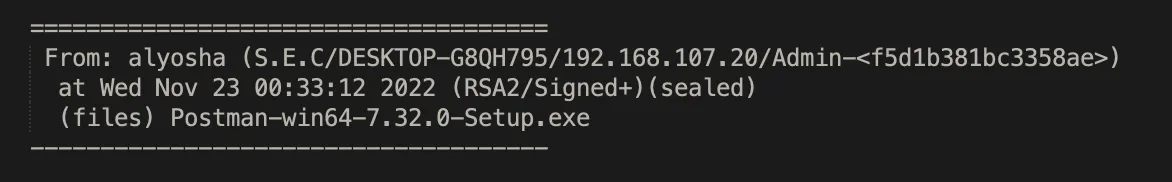
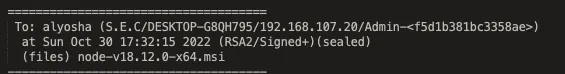
Some logs show them sharing software freely available online, such as Postman and Node, which may indicate limited access to external networks. However, at the same time we see them sharing email credentials and links to external domains that hint to at least some degree of broader internet access.
# Groups.
Lastly, extracting group names from the chat logs potentially highlights some other interesting connections. While there are 67 unique group names in total, 5-6 stand out due to potential connections to places and organizations in the DPRK.
| Abbreviation | Meaning |
|---|---|
| HUT | Huichon University of Technology |
| kutiit | Kim Chaek University of Technology |
| Uljibong | Used by multiple DPRK companies |
| SCI-TECH | Pyongyang Sci-Tech Complex |
| Chongjin Moran | Chongjin, DPRK |
# Memes.
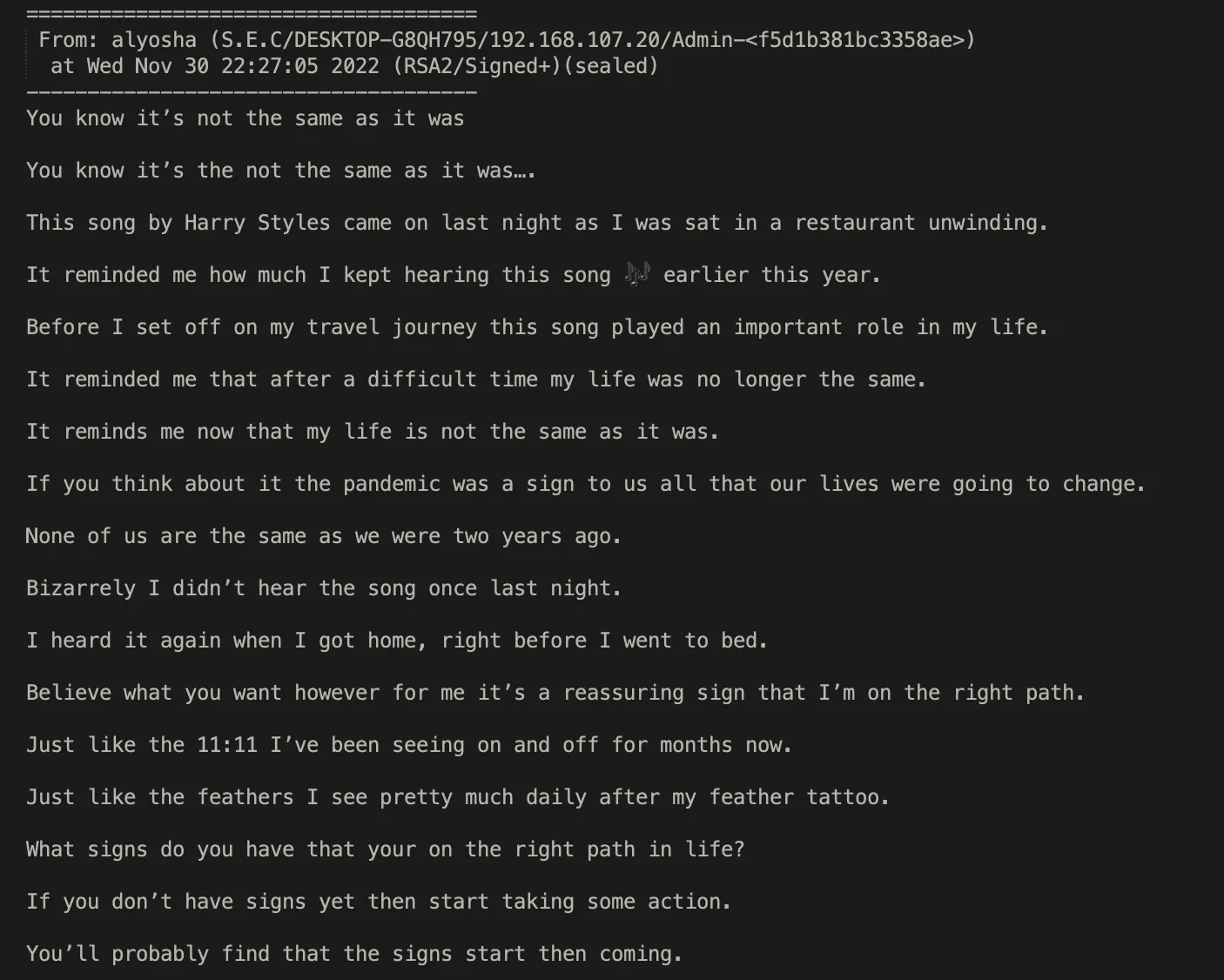
Although these chat logs lack a lot of important context, they do provide interesting insight into how North Korean IT Workers operate behind the scenes, and what their working environments are like. If you come across additional sets of logs, or any interesting information or insights regarding these logs, please reach out to us at: chollima_group@proton.me
The account information below was found in the chat logs in a way that implied ownership. It has not been vetted beyond that.
Emails:
4899432@qq.com
babakwethr@gmail.com
Chenyin1g992@gmail.com
elitedev619@gmail.com
jupiter.softdev@gmail.com
larastar721@gmail.com
laravguru@gmail.com
light.oa17@gmail.com
mmarjs22@gmail.com
partneremail@gmail.com
sp0t.s3@outlook.com
spot.jk7@gmail.com
mhcrocky@gmail.com
teacheraccount@gmail.com
thinkd.developer@gmail.com
weiyang.jin1202@gmail.com
zuhalvalmerikh@gmail.com
Github:
github.com/batmanst
github.com/bigbossphch
github.com/Blue630
github.com/dotmaker619
github.com/EliteDev619
github.com/goldenpig951204
github.com/green25dev
github.com/incredigroup
github.com/mhcatty
github.com/mhcrocky
github.com/naruhitokaide
github.com/Redmon540
github.com/sp0t/
github.com/TOP-DEVELOPER
github.com/twizard410
github.com/webstar1014
github.com/ychmdev
github.com/evilhanse
Skype:
live:.cid.8193bcc09af47e0e
