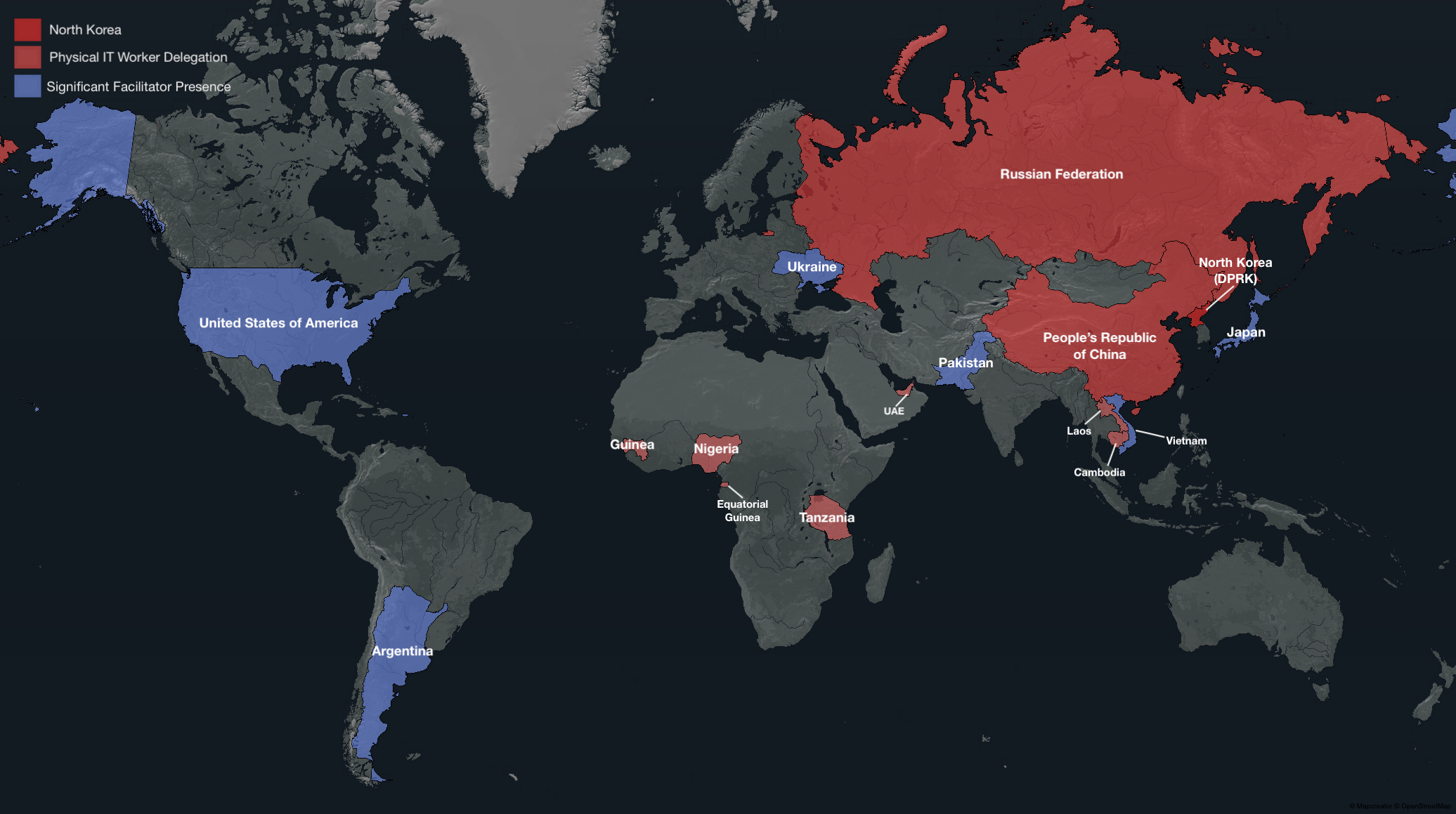
# Introduction:
On October 22, 2025, the Multilateral Sanctions Monitoring Team (MSMT), a successor to the United Nation's Panel of Experts, released an in depth report on DPRK Cyber Operations with a particular focus on IT Workers. Since the UN Panel of Experts was disbanded in 2024, the MSMT took it's place with the objective of covering North Korean sanction violation activity on an annual basis.
The MSMT report is an extremely valuable resource for understanding IT Worker operations at a strategic level. Not only did the report provide incredible insight into our own research, but it also helped validate some of our own understandings of North Koreas cyber ecosystem, and pushed us to return to old data with fresh eyes.
Since we gained so much value from being able to place our past research into a new frame, we wanted to provide a more accurate understanding to our readers of what we have documented on this site. In addition, we wanted to correct and provide additional context to a minor element of the MSMT report, and go over some pivots we made into both old and new data sources.
The full 100+ page report can be read here
## Bureau 53 (Bells Ringing in Dar Es Salaam)
Bells Ringing in Dar Es Salaam

In September of this year we did a writeup on the Tanzania based DPRK front company Bells Inter Trading and an IT Worker named Lian Hung. To our surprise, Tanzania was listed multiple times as a country where IT Workers were located even though there are potentially less than 10 working there.
Our research estimated between 9 and 11 IT Workers operating on behalf of Bells Inter Trading, depending on whether or not we believed FAMM AMTL (a company which provided work visas for some of the same individuals as Bells Inter Trading) was also involved in IT Work, or something separate.
The MSMT specifically mentioned Bureau 53 and the front company Junggongchon Trading Corporation as running IT Worker operations out of Tanzania and potentially other places in Africa. We now believe that Lian is most likely subordinate to these entities.
Bureau 53 falls under the Ministry of National Defense and has a fairly storied history. It has been primarily involved in weapons trading and operates several front companies in Vientiane, Laos and Liaoning, China, which were sanctioned a the beginning of 2025. Osong Shipping Company, Chonsurim Trading Corporation, and Liaoning China Trade Industry Co are all Bureau 53 companies that were listed in our research titled From Vientiane to Vladivostok.
In our original post we listed Haegumgang Trading Corporation as a potential front company Lian may be working under. While we no longer believe that to be the case, we wanted to note that we do still believe it possible that this corporation is involved in running IT Worker delegations in the area. This is because Haegumgang Trading Corporation is subordinate to the defense conglomerate Ryonbong General Corporation, which we have high confidence operates some of the largest IT Worker clusters around, most of which are located inside the DPRK.
### Pivoting
While the MSMT did specifically call out Tanzania, it also mentioned Equatorial Guinea, Guinea, and Nigeria as other locations IT Workers were present at between 2024-2025. Around the same time period as we identified Lian Hung, we also acquired data about an IT Worker in Guinea, a North Korean individual in Nigeria, and two teams of North Korean artists in the Persian Gulf.
Since we never had enough information for a post focusing solely on these individuals, we thought it would be best to include them here.
#### The Sun Sets in Conakry (Guinea)
As a tribute to the now defunct Pyongyang Papers and as our first pivot from Tanzania to other parts of Africa, we will look at an IT Worker who has been operating out of Conakry, Guinea, since roughly 2017. Primarily using the personas David Orion, Bill Oneil, and GenZhe Wu (potential real initials: OHC), this IT Worker has focused most of their efforts on Freelancing sites and has also developed a camera effect app previously on Apple's app store called FlippedWorld.

Social media profile picture associated with the David Orion persona

Social media profile picture associated with Bill Oneil persona. Most likely taken in 2021.

Profile picture associated with Ignatiy Blazhenov persona. Potentially taken at the North Korean embassy in Conakry, Guinea. Note: We believe this is highly likely to be another IT Worker or North Korean in Guinea and highly unlikely to be David Orion.
David has worked as a developer for the Guinean company N'deye & Tou Dista and designed websites for another Guinean company, Acti Forage SARL. N'deye & Tou Dista and Guinea Information Technology Development Corporation were directly mentioned in the Pyongyang Papers article on DPRK workers in Guinea, as were the owner's of these companies, Kalissa Aissatou and Cheick Aboubacar Traore, who acted as facilitators. Cheick Traore is also the owner of Acti Forage SARL, a drilling company who received web development work from David.

Photo of N'deye & Tou Dista front company's physical location in Conarky

N'deye & Tou Dista Offices and Cyber Cafe
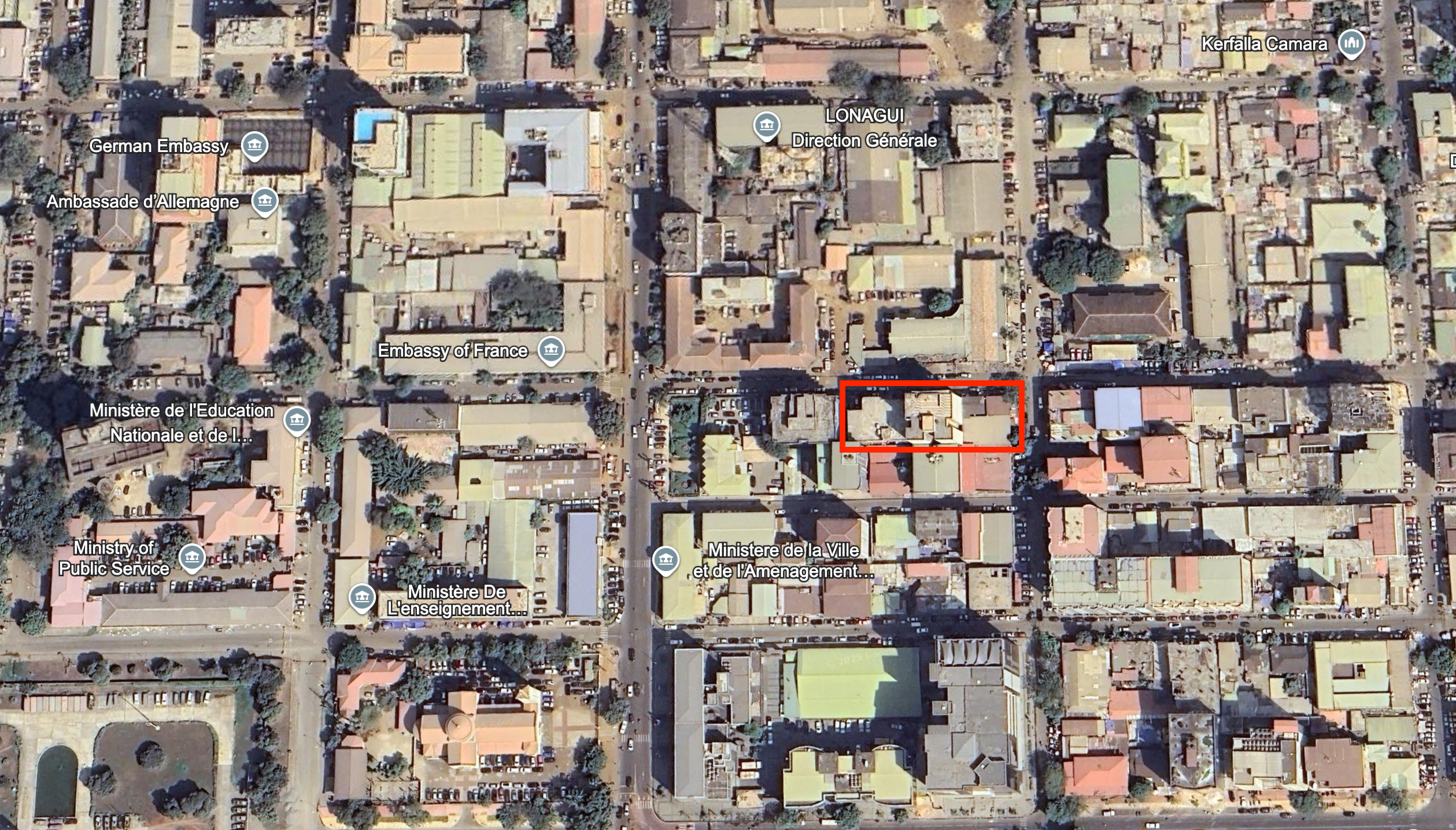
Rough location of N'deye & Tou Dista Offices (9.5107709980097, -13.711955495716307)
David has used a variety of different personas on freelancer sites, also posing as a Chinese national named Gejin Wu, an Armenian named Hrachya Ivanyan, and a British man named Bill Oneil. Through these personas, he appears to have acquired freelance work with at least one American SaaS company based in Miami. He has also listed himself as working on IPTV Development for VDC Telecom, a local telecom provider in Guinea.
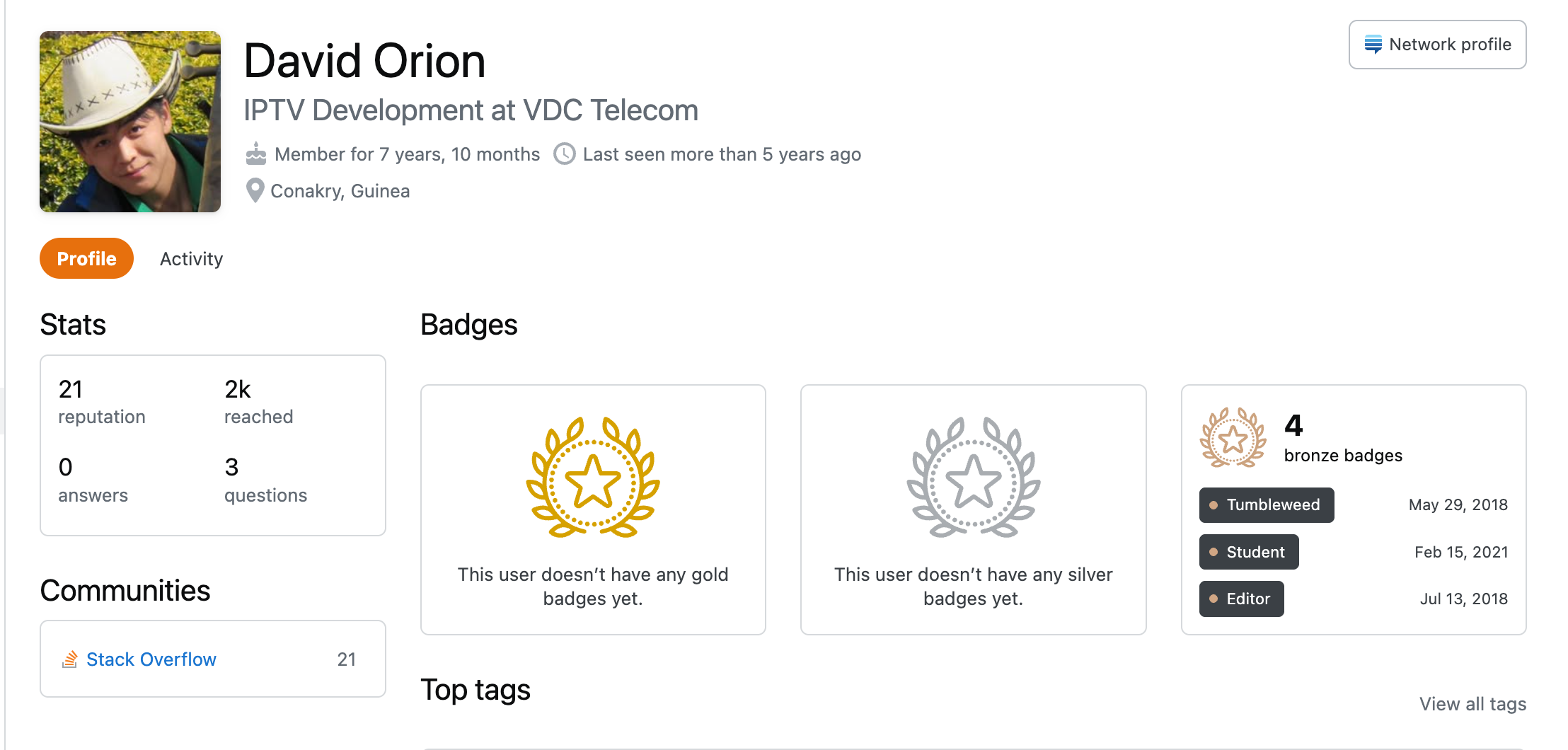
Profile of David Orion on StackOverflow
Some of our telemetry indicates that David may be working alongside a medical unit in Guinea since he made several Google searches attempting to repair an ultrasound probe. DPRK medical workers are quite active in Africa, as shown in our previous post on Tanzania, and have generally been accompanied by complaints of shoddy work and fraud.
Although David appears to have been living in Guinea since roughly 2017, we believe that he has most likely travelled back to the DPRK on several occasions. One of his emails appears in the Cutout Pro data leak coming from a Russian TransTelekom IP address associated with NetKey, software we believe is only, or primarily, used by IT Workers located inside the DPRK.
#### Rainbows in Abuja (Nigeria)

Shifting from Guinea and heading further East, we decided to cover DPRK activity in another country in Africa: Nigeria. While many in recent months have continued to see increased DPRK IT Worker activity originating from Nigerian IP ranges, we have yet to see any indication of there being IT Workers there on the ground. However, connections between Nigerian criminal groups and DPRK IT Workers have been previously observed and documented by Flashpoint.
Instead of IT Workers, we did have telemetry on a North Korean named Kim Yong Jin (KYJ), who is a representative of Korea National Insurance Company (KNIC, associated with Office 39). Insurance fraud and other related scams have been reportedly carried out by KNIC representatives, with a 2006 WSJ article stating that North Korean insurance fraud brought in tens of millions of dollars to the regime. KYJ was documented in the March 2024 UN Panel of Experts report as a potential representative of KNIC and the below companies:
Samhae Insurance Corporation
Polestar Insurance Company
Rainbow Intermediaries
In addition to this another company, Universal Insurance PLC, based in Nigeria was listed in the UN report as being a potential facilitator for KNIC. From our visibility, we believe that KNIC and Universal Insurance PLC were operating closely together, with Universal Insurance acting more as a proxy. KYJ had access to an employee email address at Universal Insurance, received memos sent to employees, and was actively instructed by KNIC to correspond with Universal Insurance for various insurance deals.
Machine translated:
나이제리아대표부 앞
// To: Nigerian Representative Office
건명: 엑쏘스중개업무건 - 여러 업무건
// Subject: Exos Brokerage Business - Various Businesses
우 건과 관련한 대표부의 2월 21일 전자우편을 언급하면서 아래와 같이 통지함.
// Regarding the February 21st email from the Representative Office regarding this matter, we hereby notify you as follows:
- 세이쉘 에덴섬 모든재산재보험
// - Seychelles Eden Island All Property Reinsurance
이 업무에 11% 참가하려고 하니 유니버썰의 참가의향을 알아보고 중개에 통지하기 바람.
// We intend to participate in this project with an 11% stake. Please inquire about Universal's interest in participating and notify the broker.
- 아르메니아 통신국 모든재산재보험
// - Armenia Telecommunications Agency All Property Reinsurance
이 업무에 18% 참가하려고 하니 유니버썰의 참가의향을 알아보고 중개에 통지하기 바람.
// We intend to participate in this project with an 18% stake. Please inquire about Universal's interest in participating and notify the broker.
- 이라크 포장재공장 모든재산재보험
// - Iraq Packaging Materials Factory All Property Reinsurance
이 업무의 보험금액이 약간 줄어든것과 관련한 수정된 결산서에 유니버썰이 수표하여 중개에 발송하였으면 본사에도 참고로 보내주기 바람. 한편 이번에 달라진 보험금액과 관련하여 삼해보험회사의 결산서를 수정하여 유니버썰에 다시 보내는 문제는 좀 더 토의한 후에 통지하려고 함.
// Universal has issued a check to the broker regarding the revised financial statements regarding the slight decrease in the insurance amount for this project. Please forward this to the head office for reference. Regarding the revised financial statements from Samhae Insurance Company regarding the changed insurance amount, we will notify you after further discussion.
- 이라크 와피르무역회사 모든재산재보험
// - Iraq Wafir Trading Company All Property Reinsurance
상기 업무의 보험금액이 크게 줄어든 조건에서 중개로부터 분양자의 수정된 재보험명세서를 받아 보내주기 바람. 그리고 이 업무의 분양자가 언급한 내용을 보면 재보험자의 참가몫에 대한 동의/거절내용은 없고 수정된 보험금액자료만 제기하였는데 중개에 문의하여 참가몫에 대한 분양자의 동의여부도 같이 확인해주기 바람.
// Given the significantly reduced insurance amount for the above project, please obtain a revised reinsurance statement from the brokerage and send it to the seller. Furthermore, the seller's statement does not indicate consent/refusal regarding the reinsurer's participation share, but only provides revised insurance amount data. Please contact the brokerage to confirm the seller's consent to the participation share.
- 유니버썰회사 신원확인자료와 3년간 재정상태표
// - Universal Company Identification Documents and 3-Year Financial Statements
대표부의 2월 15일 전자우편에서 언급한 유니버썰회사 신원확인자료와 3년간 재정상태표를 중개에 보내주었으면 본사에도 참고로 보내주기 바람.
// Please send the Universal Company Identification Documents and 3-Year Financial Statements, as mentioned in the representative office's email dated February 15th, to the brokerage. Please also send them to the head office for reference.
- 기타 미결업무들
// - Other pending transactions
방글라데슈 강철공장 건설조립 및 모든공업재보험업무, 윁남 피복공장 모든재산재보험업무, 세이쉘 싸보이개발회사(호텔) 화재재보험업무, 이라크 해상선체재보험업무들이 비교적 질이 괜찮고 보험료규모도 작지 않으므로 미결된 접수업무들이 많지만 대표부에서 이 업무들에 집중하여 분양자동의를 받도록 중개에 독촉해주기 바람.
// The Bangladesh steel plant construction and assembly and all industrial reinsurance transactions, the Vietnam garment factory all property reinsurance transactions, the Seychelles Savoy Development Company (hotel) fire reinsurance transactions, and the Iraq maritime vessel reinsurance transactions are of relatively good quality and have significant premium amounts. Therefore, there are many pending transactions. However, we request that the representative office focus on these transactions and urge the broker to obtain consent for sale.
안녕히/삼해
// Goodbye/Samhae
We found that KYJ also held credentials to Hangro, a North Korean VPN service that the NKInternet blog documented earlier this year. This is the first case where we have seen Hangro referenced by North Koreans in our dataset, which we believe may indicate it is more commonly being used by non-IT Workers abroad.
#### Murals on the Bitter Sea (Oman, UAE)

Mr. John, contact for Panorama Art Decoration LLC - Dubai
Finally, pivoting from Kim Yong Jin we found a cluster of accounts on Instagram that we have high confidence belong to a delegation of North Korean artists who appear to have worked in the Persian Gulf between 2008-2015. These workers, located in Oman and the UAE, claimed working for "Panorama Art Decoration LLC" (UAE) and "United Golden Thread LLC" (Oman), which we believe are front companies for the sanctioned entity Korea Paekho Trading Corporation.

Advertisement for United Golden Thread LLC

Advertisement for Panorama Art Decoration LLC
Korea Paekho Trading Corporation has been involved in revenue generation for the regime since the 1980s, primarily by taking on various art projects across the Middle East and Africa, such as sculpture building, and operating labour networks.

A Paekho Trading Corporation advertisement - Koryogroup
This group of artists appear to have mainly worked for private individuals at their homes in the UAE and for a number of commercial clients in Oman. They can be seen painting portraits, murals, designing building exteriors, and creating sculptures. Below we've included a selection of screenshots from their social media pages:






## Bureau 61 (From Vientiane to Vladivostok)
Returning our focus back to overlaps between our work and the MSMT, we'll look at our research on another Bureau under the Ministry of National Defense, Bureau 61.
Bureau 61 started operating IT Worker delegations around 2021 via Chinyong Information Technology Cooperation Company and is associated with the front companies "Alis LLC" (Vladivostok), "Pioneer Bencont Star Real Estate", "Shenyang GeumpungRi Network Technology Company Limited", and Umnal.
Based on MSMT reporting, we believe that our research titled From Vientiane to Vladivostok, and pictures posted by members of our broader collective, were primarily of IT Workers subordinate to Bureau 61's Chinyong Information Technology and it's front companies Alis LLC, Umnal, and Pioneer Star Bencont Real Estate. Our original belief was that they may be a part of Bureau 53, as stated at the beginning of that post.

Pioneer Bencont Star Real Estate/Umnal IT Workers - Jenson Collins, Keisuke Watanabe, and Kazune Takeda at Azor Sharkin Restaurant, Vientiane, Laos

Pioneer Bencont Star Real Estate/Umnal IT Workers - Jenson Collins and an unidentified IT Worker at Azor Sharkfin Restaurant, Vientiane, Laos

Pioneer Bencont Star Real Estate/Umnal IT Workers - Naoki Murano and Seo Sigoto bowling at Parkson Mall in Vientiane

Pioneer Bencont Star Real Estate/Umnal IT Workers - Seo Sigoto and Jenson Collins at an AirBnB in Laos

Pioneer Bencont Star Real Estate/Umnal IT Workers - Jenson Collins, Keisuke Watanabe, Seo Sigoto, and an unidentified IT Worker playing volleyball at Victory Fields in Laos
The MSMT Report states that the group of IT Workers in Laos subordinate to Bureau 61 operated under the front company Pioneer Star Bencont Real Estate, which was previously based in Dubai.
In 2022 and 2023, the UN Panel of Experts reported on an IT Worker named Oh Chung Song (OCS). A resident of Dubai, OCS worked with eight other DPRK IT Workers and when uncovered by their employer in 2021 as being North Korean, fled to Vientiane, Laos. While OCS left to the DPRK in February 2023, six of the other individuals he fled to Vientiane with stayed behind and left later in 2023. Four of them are pictured below.

From what we can piece together, we believe that Pemba Sherpa (Kim Kwang Jin), Charles Palmer (Kang Tae Bok), and Bryan Cho (Jong Pong Ju) are also Bureau 61 workers, most likely under the Umnal front company. Both were seen later on in Vladivostok alongside Choe il-Kuk aka Naoki Murano:

Choe il-Kuk/Naoki Murano and Jenson Collins eating dinner at Yoree Korean Restaurant in Vientiane, Laos
Between mid to late 2023, it seems that most of the IT Workers we were tracking had relocated back to Vladivostok under the Chinyong front companies Umnal and Alis LLC. While we had a gap in visibility for most of 2023, February 2024 is where we see most of these IT Workers from Laos come together in Vladivostok with a much larger group. We identified a large number of the North Koreans pictured below as IT Workers and now believe that they all mostly fall under Alis LLC (with the exception of those from Laos):

Bottom row, right to left - Choe Il-Kuk (Naoki Murano), Seo Sigoto, Kang Tae Bok (Joshua Palmer), unknown Umnal IT Worker, Kim Kwang Jin (Pemba Sherpa), Jong Pong Ju (Bryan Cho) in Vladivostok, Russia

Note: We have medium confidence that the individual highlighted above is Kim Sang Nam, the head of Chinyong Information Technology Cooperation Company. He was seen with Umnal IT Workers in both Laos in 2021 and Vladivostok in 2024

Bottom row, third from right - Karlo Lee Chan AKA Leech Dev, Above (left of white jacket) - Gerardo Salgado, Above (clapping, black jacket) - Kenneth Francis, Right (brown jacket) - Daiki Saito

Thanks to ZachXBT (src) | Bottom row, left to right - Andy Bell, Danny Jin, Eric Andrade
Note: Andy Bell, pictured above on the far left, appears to have previously resided in Dalian, China and relocated to Vladivostok roughly around the same time as Pioneer Star Bencont Real Estate members did from Laos. This may mean that he was previously a part of Chinyong front company in Shenyang, China - Shenyang GeumpungRi Network Technology Co. Ltd
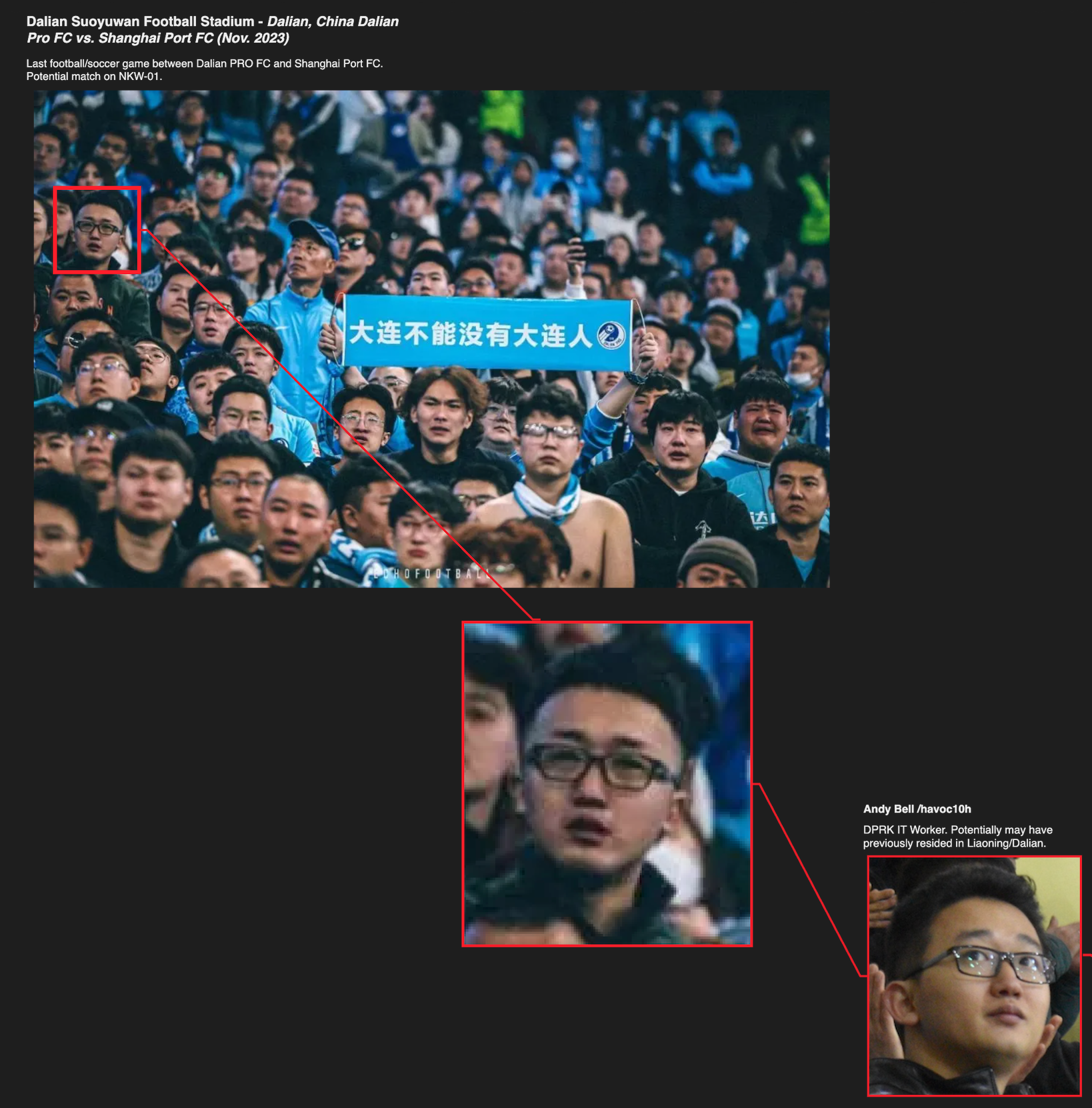
In July of 2024 and May of 2025 we identified more images of the same cluster of Chinyong IT Workers:

July 2025, Chinyong Information Technology workers in Vladivostok, Russia

July 2025, Chinyong Information Technology Workers

May 2025, Chinyong Information Technology Workers - Naoki Murano, Kazune Takeda, and another IT Worker from Laos can be seen in white shirts

Credit: Tayvano | May 2025, Chinyong Information Technology Workers mapped to online personas
Throughout 2024 and 2025, we frequently observed members of Chinyong Information Technology in Vladivostok appear in conversations with partners, indictments, and sanctions. While there are a vast number of IT Workers outside of Vladivostok, we found it especially interesting how many familiar faces continued to appear over and over again.
While this could be due to our own biases, from our perspective it appears that Chinyong IT Workers may have been some of the most prevalent amongst large enterprises and the cryptocurrency sector during the 2024-2025 time period. In May 2025 we observed another member of Chinyong using the persona Steven Smith get interviewed by the cryptocurrency company Kraken, whose interview was broadcast on CBS. Prior to the MSMT Report, this was the last major coverage we saw of Chinyong.
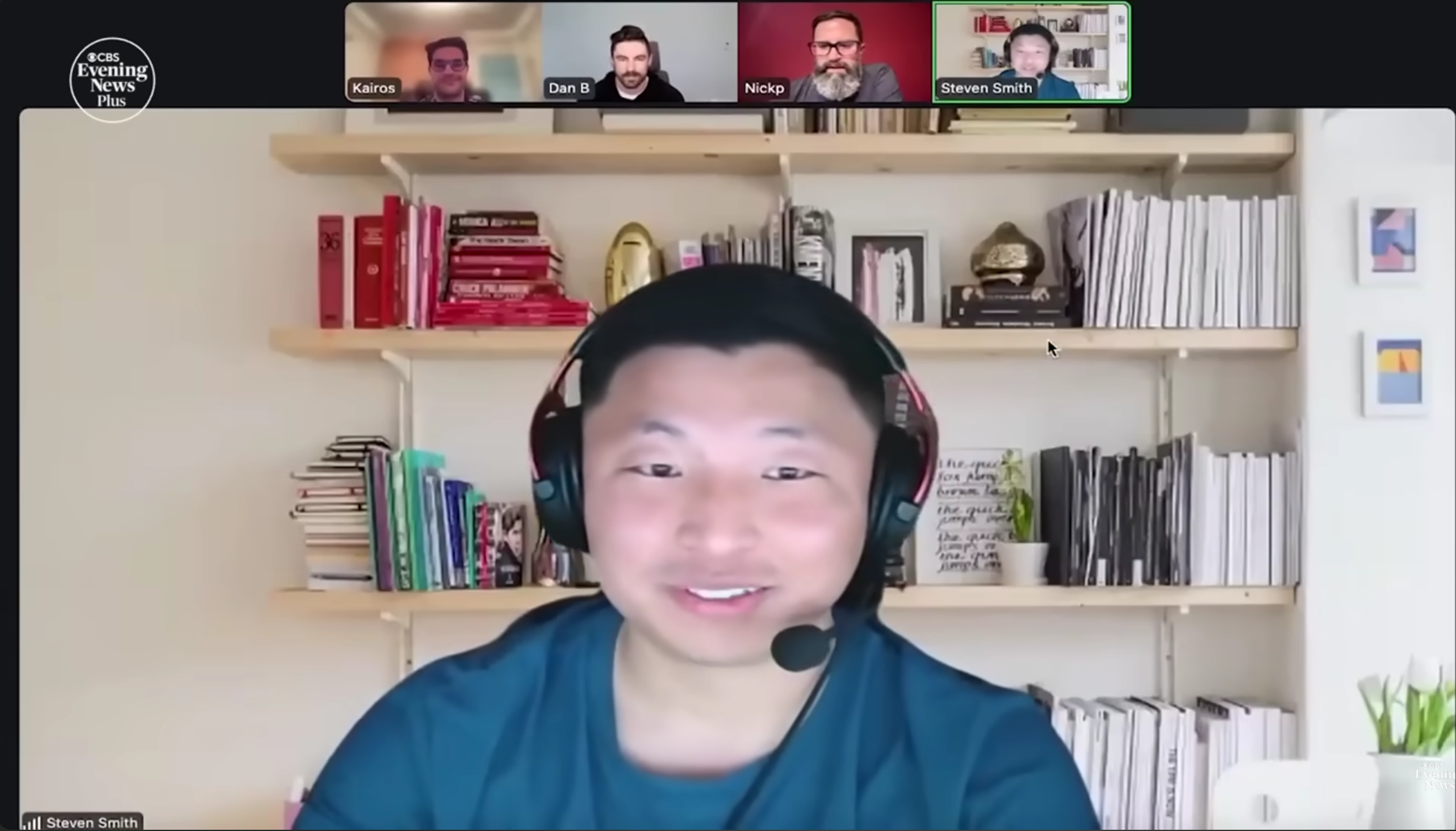

Lastly, we would also like to thank the authors of the MSMT for citing our work and specifically providing Naoki Murano's real name.
## Righting Wrongs (Dubai, Crypto, Moonstone Sleet, and the Pivot Odyssey)
Dubai, Crypto, Moonstone Sleet, and the Pivot Odyssey
Although the MSMT proved to be a wealth of extremely valuable information, there was one minor mistake that we wish to correct.
In August 2025 we released a piece of research titled *Dubai, Crypto, Moonstone Sleet, and the Pivot Odyssey* which was the product of months of work. The main subject of this research was on a cluster of IT Workers we believe are closely aligned with, or potentially members of, the APT group Moonstone Sleet.
Moonstone Sleet originally made headlines after using several chained zero days in Chrome to target crypto developers who were lured to a fake cryptocurrency project created by Moonstone Sleet titled "DeTankZone".
In Kaspersky's coverage of this campaign, they noted that the DeTankZone webpage was hosting chained Chrome zero day exploits and also covered the actual game that went along with the lure. They went on to say that the DeTankZone game was actually a copy of a "legitimate" game called DefiTankLand.
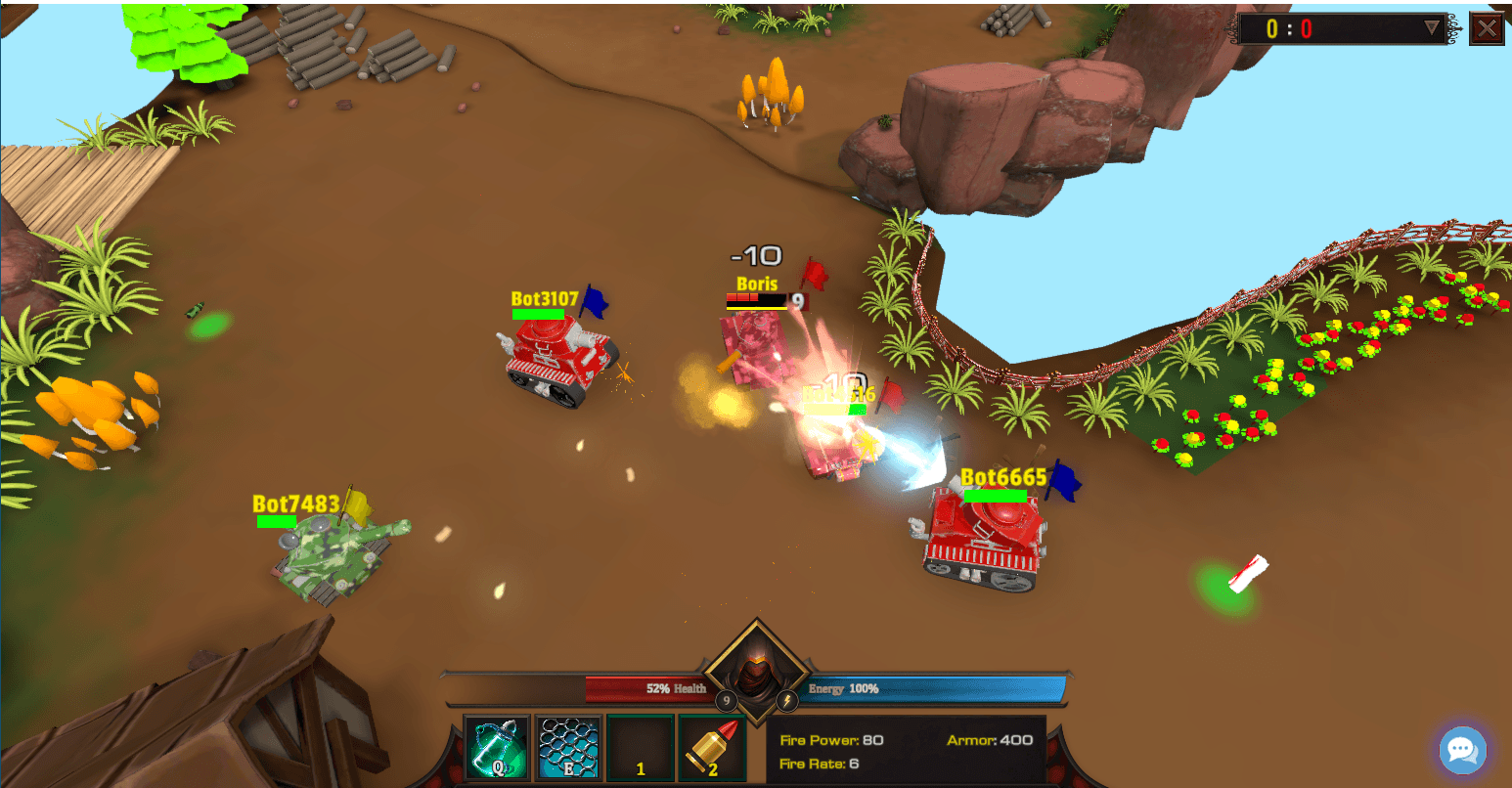
Screenshot of the DefiTankLand/DeTankZone game
After reading Kaspersky's reporting on Moonstone Sleet, we began looking into DefiTankLand and discovered that it was not legitimate at all, but was actually created by a cluster of IT Workers that we dubbed BABYLONGROUP. Our research focused heavily on documenting this cluster and led to us identifying that some of its members worked for a front company that partnered with Atari, that a Chinese crypto OTC Broker who was embedded with the group runs an underground criminal market, and.connections to a Bureau 53 IT Worker in Tanzania which we already covered.
While this is ultimately a minor error (and in the long run does not affect anything), since the IT Worker cluster behind DefiTankLand have a particularly fascinating story we felt it necessary to include a section correcting this error.
(Defitankland is not a legitimate game. Defitankland is made by North Korean IT Workers)
Farewell!

2023 - Chinyong/Alis LLC IT Workers celebrating New Years in Vladivostok
## IOCs
The Sun Sets in Conarky (Guinea - DavidOrion999)
Emails:
---------------------------------
davidorion999@gmail.com
loyalprince55555@outlook.com
billoneillighttiger@gmail.com
johnwoo829612@outlook.com
johnwoo82921323@gmail.com
johnjohnjohn829612@outlook.com
johnjohnjohn829612@hotmail.com
johnwooaugtwe@hotmail.com
andon211bala@yahoo.com
blazhenov525@gmail.com
annaparova989@outlook.com
joanahillora843@outlook.com
makdanger11220@outlook.com
makdanger3434@outlook.com
maksim1029lv@outlook.com
maksimbrave1030@gmail.com
maksimbrave1030@outlook.com
romancondo1278@outlook.com
safranov512@yahoo.com
slavomir829@hotmail.com
slavomir829612@hotmail.com
slavomir829612@outlook.com
talenteddeveloper098@gmail.com
hrachya1995dev@gmail.com
hrachya1995dev@outlook.com
ivanyanhrach1995@gmail.com
ivanyanch19891111@gmail.com
shyam6191@gmail.com
Socials:
---------------------------------
https://www.linkedin.com/in/yin-xing-50b95b186
https://www.linkedin.com/in/bill-oneil-1b24a81a9
https://hk.linkedin.com/in/yinxing-gao-7b4471189
Freelance Profiles:
---------------------------------
https://www.upwork.com/freelancers/~018fb2be2f5f7d4d72
https://www.upwork.com/freelancers/~01fd27fe1020f685a7
https://www.fiverr.com/greatemperor999
https://hubstafftalent.net/profiles/gao-yinxing
https://hubstafftalent.net/profiles/gao-yinxing-2
https://hubstafftalent.net/profiles/yinxing-gao
https://hubstafftalent.net/profiles/hrachya-ivanyan
https://clay.earth/profile/yinxing-gao
Personas:
---------------------------------
David Orion
Bill Oneil
Blazhenov Ignatiy
GenZhe Wu
GeJin Wu
John Woo
Maksim Lobanov
Slavomir Bojanic
Gao Yinxing
Hrachya Ivanyan
Hrachya Ivan
Fronts:
---------------------------------
LP Dev Team
lpdevteam.com
Qihang Software
https://qihangsoftware.com/#team
N'deye & Tou Dista
https://ndeyetoudista.com/#about
https://www.facebook.com/people/Ndeye-TOU-DISTA
Wasaya Business
https://wasaya-business-gn.com/services/#team
Acti Forage SARL
acti-forage-gn.com
Rainbows in Abuja (Nigeria - Kim Yong Jin)
Emails:
---------------------------------
darkb761216@gmail.com
dragonrhm0817@gmail.com
star710928@gmail.com
yz.demix@gmail.com
marketing.rep@universalinsuranceplc.com
shojokur@gmail.com
Personas:
---------------------------------
Penguin Ui
hong kong
Pen Ui
Fronts/Facilitators:
---------------------------------
Universal Insurance PLC
Millbank Brokers
Murals on the Bitter Sea (Oman, UAE)
Emails:
---------------------------------
paekhouae@yahoo.com
omanpaekho@yahoo.com
Personas:
---------------------------------
Mr. John
Cool Hyun Sun
Fronts/Facilitators:
---------------------------------
United Golden Thread LLC
Panorama Art Decoration LLC
From Vientiane to Vladivostok (Laos, Russia)
Emails:
---------------------------------
thongloundevsoft717@gmail.com
supermutec11@outlook.com
supermutec12@outlook.com
pisoft314@gmail.com
IPs:
---------------------------------
183.182.105.91